The malware has the potential to target large-scale victims since games like Super Mario 3 are famous among and adored by children around the world.
Recently, Cyble researchers discovered a trojanized version of the Super Mario 3: Mario Forever installer. The malware hidden inside the installer can perform various malicious tasks, such as stealing sensitive data, deploying cryptocurrency miners, and launching ransomware.
Beware of Fake Super Mario 3 Installer
Researchers have noted that game installers have emerged as a lucrative way to maximize monetary gains. Threat actors prefer to exploit game installers for delivering malware due to their extensive user base, powerful hardware, and large file size, which allows them to easily hide malware. Gamers trust these installers, considering them legitimate software, but social engineering can allow attackers to exploit this trust and trick gamers into downloading malware.
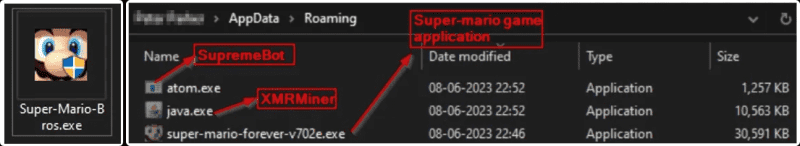
In this case, the researchers wrote that the fake installer comes with three executable files. One of these files installs the game, while the other two files, titled java.exe and atom.exe, are installed in the AppData directory on the device. Both files are assigned different tasks.
- Java.exe- it may look like a regular Java runtime, but in reality, it is a Monero cryptocurrency miner tasked with establishing a connection to a mining server (gulfmonerooceanstream).
- Atom.exe- It is a self-duplicating SupremeBot mining client that creates a scheduled task for executing the copy every fifteen minutes. SupremeBot has to fetch another executable, “wime.exe,” after establishing a connection to a C2 server.
How does it work?
After the malicious installer file “super-mario-forever-v702e” is installed on the system, it launches an XMR miner and a SupremeBot mining program through two files. Once this is done, a connection to the C2 server is established to transmit data information, register the client, and obtain the required configuration to start cryptocurrency mining. This is followed by fetching the “wime.exe” executable, an open-source Umbral Stealer.
The Umbral Stealer is capable of stealing sensitive user data from the targeted device, which includes stored cookies and passwords, session tokens, credentials from cryptocurrency wallets, and authentication tokens for other platforms or games. Additionally, it disables Windows Defender to evade detection if tamper protection is inactive. However, if tamper protection is active, it adds the process to the exclusion list.
Potential Dangers
The malicious Super Mario 3 installer is quite lethal as it is capable of cryptocurrency mining and data stealing. This can result in heavy financial losses for victims and drain computer resources, causing a decline in system performance.
“Malware distributed through game installers can be monetized through activities like stealing sensitive information, conducting ransomware attacks, and more,” Cyble’s report read.
