Cybercriminals have started employing a new phishing attack that abuses the popularity of Google Drive and Docs to bypass security filters.
In a report published by the IT security researchers at Avanan, it has been revealed that threat actors are using a Google Docs exploit in a new phishing campaign.
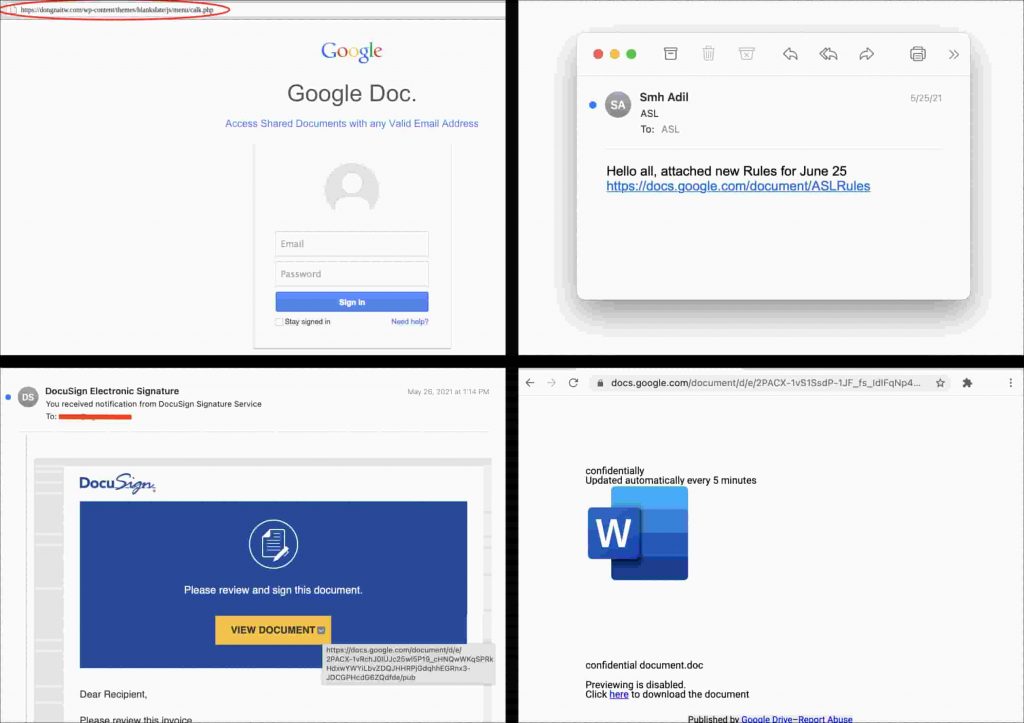
The researchers explained how an attacker writes a webpage resembling that of Google Docs sharing page and uploads it on Google Drive which scans the file and automatically renders the HTML. Then, that file is opened through Google Docs where the attackers get the top version with the rendered images.
The link is then generated is attached to emails and sent to the victims where they are asked to download the document. Once that link is clicked, they are redirected to the actual malicious phishing website where their credentials will be stolen through another web page made to look like the Google Login Portal.
Although some attackers have tried using the functionality of legitimate services to further their own malicious goals such as the spoofing of a DocuSign document which took the user to a fake DocuSign login page, according to researchers, this was the first time where such a popular service like Google was exploited.
Google Docs is used very sophistically in this manner and attackers end up with a good chance of bypassing static link scanners that many legacy security products use.
Moreover, it is always a good idea to not open any Google Docs link shared with you until you can confirm that it will actually lead you to Google Docs and is not some third-party pretending to be like Google Docs.
In a blog post, Avanan’s Jeremy Fuchs wrote that:
Hackers are bypassing static link scanners by hosting their attacks in publicly known services. We have seen this in the past with small services like MailGun, FlipSnack, and Movable Ink but this is the first time we’re seeing it through a major service like Google Drive/Docs.
This attack highlights how important it is to use a multi-tiered security architecture like Avanan because these attack emails can be caught by Avanan’s AI’s understanding of an organization’s email behavior.
As for Google Drive; this is not the first time when the service has been abused for malicious purposes. Previously, malware and phishery tool like DarkHydrus was also being spread through Google Drive.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.