The new Agent Tesla variant exploits CVE-2017-11882/CVE-2018-0802 vulnerability to execute the malware.
Key Findings
- A new variant of the Agent Tesla malware family is being used in a phishing campaign.
- The malware can steal credentials, keylogging data, and active screenshots from the victim’s device.
- The malware is spread through a malicious MS Excel attachment in phishing emails.
- The malware exploits an old security vulnerability (CVE-2017-11882/CVE-2018-0802) to infect Windows devices.
- The malware ensures persistence even when the device is restarted or the malware process is killed.
New Agent Tesla Variant Detected in Malicious Phishing Campaign
FortiGuard Labs threat researchers have detected a new variant of the notorious Agent Tesla malware family used in a phishing campaign. Report author Xiaopeng Zhang revealed that the malware can steal “credentials, keylogging data, and active screenshots” from the victim’s device. Stolen data is transferred to the malware operator through email or SMTP protocol. The malware mainly infects Windows devices.
For your information, Agent Tesla malware is also offered as a Malware-as-a-Service tool. The malware variants use a data stealer and .NET-based RAT (remote access trojan) for initial access.
How Phishers Trap Users?
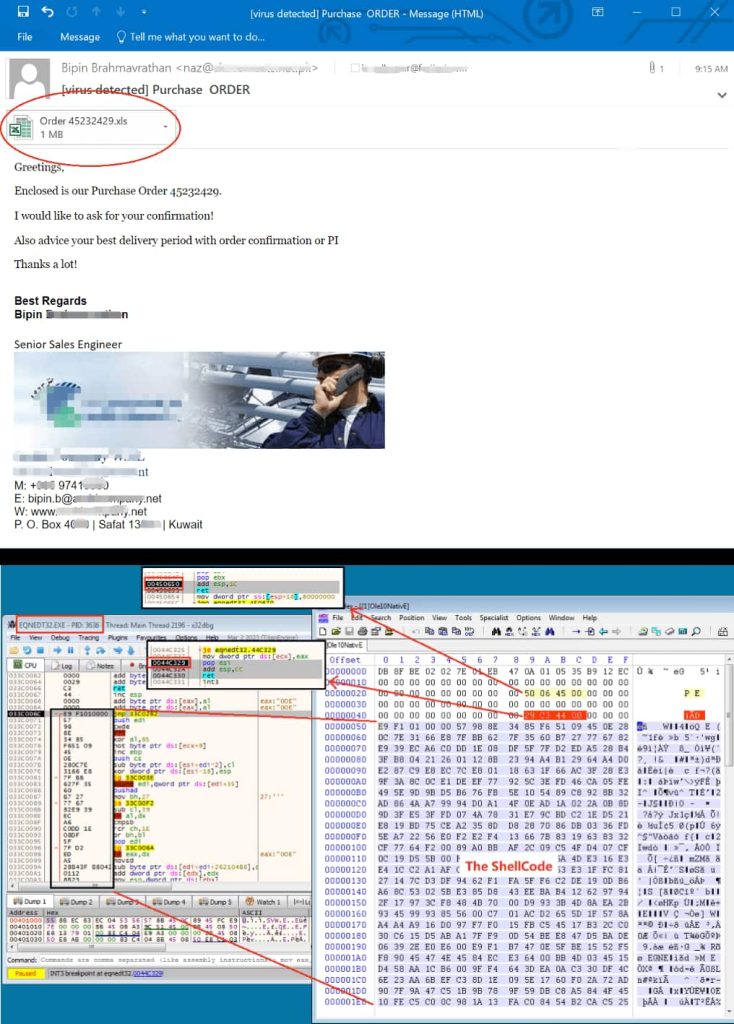
This is a phishing campaign, so initial access is gained through a phishing email designed to trick users into downloading the malware. The email is a Purchase Order notification that asks the recipient to confirm their order from an industrial equipment supplier.
The email contains a malicious MS Excel attachment titled Order 45232429.xls. This document is in OLE format and contains crafted equation data that exploits an old security RCE vulnerability tracked as CVE-2017-11882/CVE-2018-0802 instead of using a VBS macro.
This vulnerability causes memory corruption in the EQNEDT32.EXE process and allows arbitrary code execution through ProcessHollowing method, in which a hacker replaces the executable file’s code with malicious code.
A shellcode download/execute the Agent Tesla file (dasHost.exe) from this link “hxxp://2395.128.195/3355/chromium.exe” onto the targeted device. It is a .NET program protected by IntelliLock and .NET Reactor. Relevant modules are encrypted/encoded in the Resource section to prevent its core module from detection and analysis.
It is worth noting that Microsoft released fixes for this vulnerability in November 2017 and January 2018. However, it is still being exploited by threat actors indicating the presence of unpatched devices. Per FortiGuard research, they observe around 1300 vulnerable devices daily and mitigate 3,000 attacks at the IPS level per day.
Analysis of Agent Tesla Activities
According to FortiGuard Labs’ report, published on 5 Sep 2023, Agent Tesla variant steals stored credentials from web browsers, email clients, FTP clients, etc. There is a long list of targeted software and email clients available here.
The malware sets a keyboard hook through the API SetWindowsHookEx() to monitor low-level keyboard inputs and calls the callback hook procedure “this.EiqpViCm9()” whenever the victim types something on the device. The malware steals the program title, time, and input contents at regular intervals. A Timer calls a method to check the log.tmp file every 20 seconds and sends the info to the attacker via STMP. Moreover, the malware uses another Timer with a 20-minute interval to check for device activities and determine when to capture screenshots.
How does Agent Tesla maintain persistence?
Agent Tesla malware ensures persistence even when the device is restarted, or the malware process is killed, using two methods. It either executes a command for creating a task in the TaskScheuler system in the payload module or adds an auto-run item in the system registry. These methods allow duplication of dasHost.exe to launch automatically when the system restarts.
Protection against such campaigns
Be suspicious of any email that asks for your personal or financial information: Phishing emails often try to trick you into giving up your passwords, credit card numbers, or other sensitive information. Never click on links or open attachments in emails from senders you don’t know or trust.
Keep your software up to date: Software updates often include security patches that can help protect you from malware. Make sure to install security updates as soon as they are available.
Use a strong antivirus and anti-malware program: Antivirus and anti-malware programs can help detect and remove malware from your computer. Keep your antivirus and anti-malware programs up to date and scan your computer regularly.
Be careful what you click on: Phishing emails often contain links that lead to malicious websites. If you click on a link in an email, make sure to check the URL carefully before visiting the website.
Use a spam filter: A spam filter can help reduce the number of phishing emails that you receive.
Educate yourself about phishing: The more you know about phishing, the better you will be able to spot it. Read up on phishing scams and how to protect yourself.
RELATED NEWS
- Hackers leak logins of vulnerable Fortinet SSL VPNs
- Hackers Using Stolen Ivacy VPN Certificate To Sign Malware
- Smoke Loader Drops Location Tracker Whiffy Recon Malware
- Luna Grabber Malware Hits Roblox Devs Using npm Packages
- Chae$4 Malware Steals Login, Financial Data from Businesses
- Adobe ColdFusion Vulnerabilities Exploited to Deploy Malware