For as long as we can remember, Android has been continued to be successfully targeted in malware attacks, mostly through malicious apps. This represents a long term threat to the platform when competing against iOS.
Now, in another incident, recently, Kaspersky has identified a malware campaign dubbed PhantomLance that is actively attacking Android users within Asia and beyond.
Believed to be originating from OceanLotus or ATP32; a Vietnamese state-backed advanced persistent threat (APT) group that has been operating since 2013, the campaign functions through numerous apps both within the Google Play Store and third-party stores such as APKpure.
The data it can collect once the victim is infected includes their location, call logs, SMS history, contacts, the phone model, the OS version running, and also a list of other installed apps on the phone.
See: New Android malware on Play Store disables Play Protect to evade detection
The reason it may be looking at the latter two is that upon installation, the malware adapts accordingly which according to the researchers helps,
“The actor…avoid overloading the application with unnecessary features and at the same time gather information needed.”
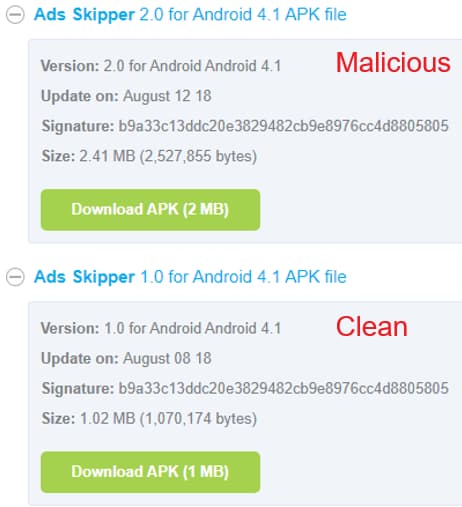
An example of one such malicious application:
Moreover, the malware was being deployed using three different types of samples of code which the attackers termed as version 1, version 2, and version 3 with the latter most being the most sophisticated. This does not mean that the version numbers indicate any kind of chronology as they were found to be deployed throughout various periods of time overlapping with each other.
In order for the attackers to avoid detection, they employed a range of measures differing version wise. Firstly, all of the apps had a clean version uploaded initially but then malicious code was added later in the updates that followed which allowed the attackers to avoid appearing suspicious.
Secondly, hackers also created fake developer profiles on Github to add an aura of legitimacy to the apps. Coming to the code, the researchers state in their blog post how,
“No suspicious permissions are mentioned in the manifest file; instead, they are requested dynamically and hidden inside the dex executable.”
Commenting further, they explain, “if the root privileges are accessible on the device, the malware can use a reflection call to the undocumented API function “setUidMode” to get permissions it needs without user involvement”. The only caveat is that this particular technique does not work on versions below Android SDK 19.
See: Fake Coronavirus apps hit Android & iOS users with spyware, adware
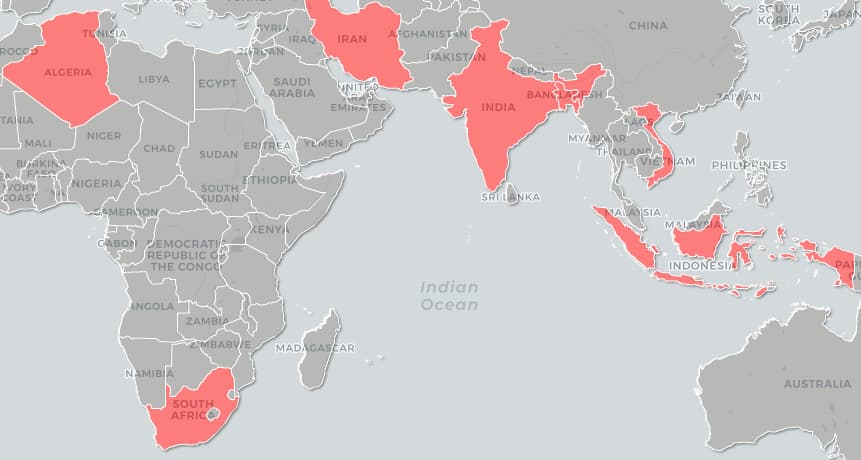
However, despite all of these techniques, it seems to have only infected about 300 users spread across Vietnam, India, Bangladesh, Indonesia, Algeria, South Africa, Nepal, Myanmar and Malaysia with some of these specifically targeting Vietnam – no surprise since it is the most attacked country in this regards.
To conclude, Google has currently removed the reported apps but we can expect the campaign to continue with further infections.
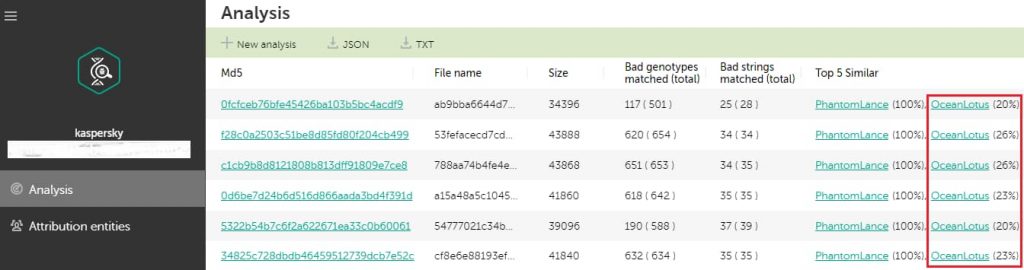
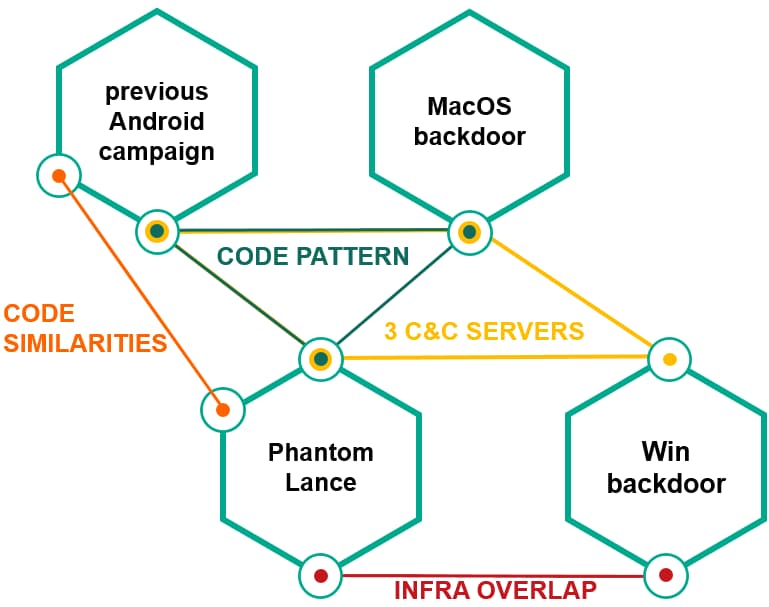
Additionally, an Android malware campaign that was functioning between 2014-2017 and was attributed to the same group is believed to have a payload similarity of at least 20% with the current ones at hand.
This has led Kaspersky to attribute the earlier campaign to OceanLotus with “medium confidence” citing infrastructure overlaps as well.
All of this is best summarized in the words of a security researcher at Kaspersky – Alexey Firsh – who states that “this campaign is an outstanding example of how advanced threat actors are moving further into deeper waters and becoming harder to find.”
See: Hamas hackers posed as women to con IDF into downloading malware
Elaborating further, “PhantomLance has been going on for over five years and the threat actors managed to bypass the app stores’ filters several times, using advanced techniques to achieve their goals. We can also see that the use of mobile platforms as a primary infection point is becoming more popular, with more and more actors advancing in this area”.
Android users can always make use of a good anti-virus program as we usually advise and especially steer clear away from third-party app stores. The reason is pretty obvious if a company like Google with all its resources cannot ensure complete security on its own app store, others are less likely to be able to do so becoming a hotspot for malicious applications.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.