Job seekers and recruiters should be vigilant for malicious emails and messages on LinkedIn, where TA4557 threat actors feign interest in a job, but their actual intent is to deliver a backdoor.
TA4557, a skilled yet mysterious cybercriminal group, has been targeting recruiters with malware since October 2023, as revealed in the latest report from Proofpoint published on 12 December 2023.
According to Proofpoint’s research, TA4577 sends direct emails to recruiters to deliver malware. These emails appear benign, expressing interest in an open job. When the recipient replies, that’s when the attack chain begins.
TA4557 is a financially motivated threat actor known to distribute the More_Eggs backdoor against recruiters on LinkedIn. For most of 2022 and 2023, the threat actor applied to existing open job listings and embedded malicious URLs in the application.
However, they have changed tactics in the latest campaign where they utilize both the new method of sending direct emails and the older technique of applying to jobs posted on public job boards, but the intention remains the same.
In early November 2023, security vendor Proofpoint observed campaigns where TA4557 directed recipients to refer to the domain name of their email address to access their portfolio instead of sending the resume website URL directly. The actor then directed victims to a personal website mimicking a candidate’s resume or job site that used filtering to redirect users to the next stage of the attack chain.
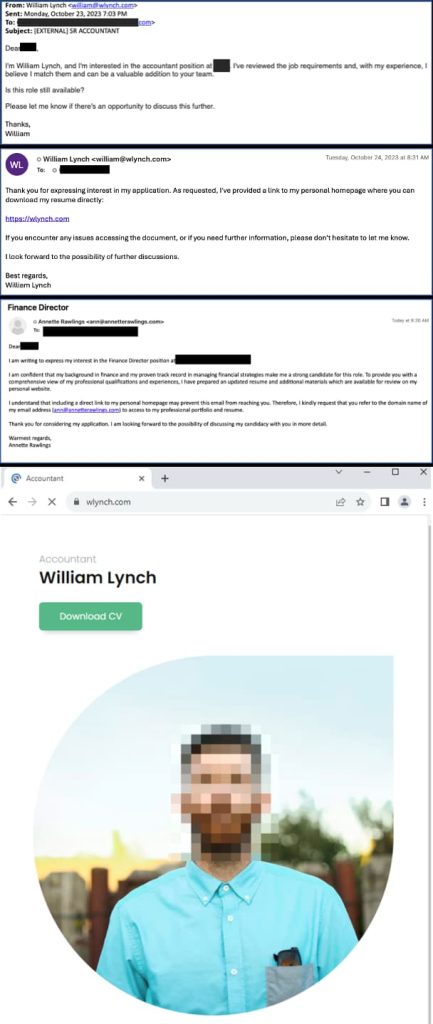
Once the victim passes filtering checks, they are taken to a resume in plain text or a candidate website, which uses a CAPTCHA to initiate the downloading of a shortcut file (.LNK) that abuses legitimate software functions to download/execute a scriptlet called Living Off The Land (LOTL).
This script decrypts and drops a DLL to create a new regsrv32 process using WMI (Windows Management Instrumentation) and uses multiple checks to determine whether the DLL is being debugged. This DLL also drops the More_Eggs backdoor and initiates the creation of the MSXSL process using the WMI service.
As per Proofpoint’s report, TA4557 is unique due to its unique tool/malware usage, campaign targeting, job candidate-themed lures, sophisticated evasive measures, distinct attack chains, and actor-controlled infrastructure. this group’s activity has historically overlapped with cybercrime group FIN6 activities and the malware suite used by cybercrime groups Cobalt Group and Evilnum.
TA4557 demonstrates sophisticated social engineering, designs its lures to legitimate job opportunities posted online, uses benign messages to build trust and engages with targets before sending malicious content.
The group regularly changes its sender emails, fake resume domains, and infrastructure, which makes it difficult for defenders and automated security tools to detect the content as malicious.
Therefore, organizations using third-party job posting websites should be aware of TA4557’s tactics and educate employees regarding this threat, especially in recruiting and hiring functions.
RELATED ARTICLES
- Hackers used fake job website to scam jobless US veterans
- Hackers leak data of 29 million Indian job seekers for download
- A UK recruitment firm exposed sensitive applicants data for months
- Hackers Used Fake LinkedIn Job to Hack Off $625M from Axie Infinity
- Interpol Busts Human Traffickers Luring Victims with Fake Online Job Ads
