The Rich Communication Services (RCS) messaging standard is used by almost every phone carrier around the globe, which clearly explains its significance for mobile phone users. Now a set of vulnerabilities is threatening the service.
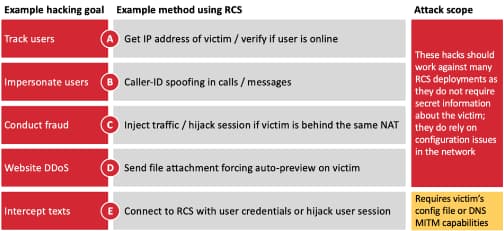
According to security researchers at SRLabs (Security Research Labs), the way phone carriers are implementing the RCS standard is flawed and the vulnerabilities can make users susceptible to all kinds of attacks such as call interception, text message, location exposure, and spoofing of phone numbers, etc.
See: How a man hacked his victims’ SIM cards to steal millions of dollars
This is indeed a concerning situation since large enterprises such as Vodafone are using flawed procedures and technology and are making hundreds of millions of people vulnerable to data exposure, stated SRLabs’, Karsten Nohl.
This standard is believed to be a better substitute for SMS but this research reveals that even the most modern protocols aren’t safe from exploitation if there is even the slightest glitch, making phone network security an issue of concern.
According to Verge, RCS standard is introduced to replace SMS and supports a number of new features that messaging clients like WhatsApp and iMessage offer such as typing indicators end-to-end encryption and read receipts. It is a cross-platform messaging standard that any phone carrier company can easily integrate.
It is worth noting that researchers didn’t identify any flaws in the RCS standard but the way carriers are implementing it while issuing SIM cards.
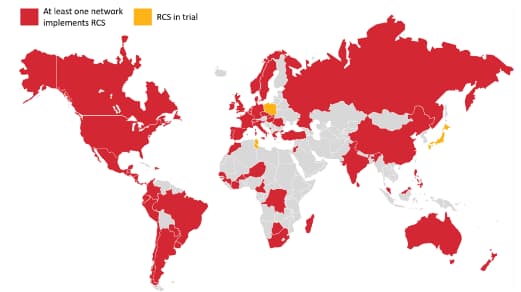
Researchers assessed SIM cards issued by different carriers to reach their analysis. In one of the samples, they identified that wrongful implementation of the RCS standard allowed any application on the users’ phone to download the standard’s configuration file leading to data exposure. The app gained access to username and password and was able to manipulate text messages and voice calls.
In another SIM researchers noticed that the 6-digit code used by a phone carrier to authenticate a user’s identity was vulnerable to be exposed via a brute force attack launched by a third-party.
Video demonstration of RCS flaws:
SRLabs didn’t specify the vulnerabilities in the way RCS standard is implemented or the carriers responsible for wrongly implementing it but the company did reveal that at least 100 phone carriers (majority from Europe) are implementing it including four of the major carriers in the US.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
