The online version control and code distribution platform Github has suffered a series of massive distributed denial of service (DDoS) attacks on Wednesday, February 28, 2018, causing service disruption by forcing its website Github.com to go offline.
In the first phase of the attack, Github’s website suffered a shocking 1.35 terabits per second (Tbps) spike while in the second phase Github’s network monitoring system detected 400Gbps spike. The attacks lasted for over 8 minutes and due to the massive traffic used by the attacks, this is the largest DDoS attack ever witnessed.
Previously, the French telecom OVH and Dyn DNS suffered the largest DDoS attacks with 1 Tbps traffic flow. Both attacks were carried by hackers using Mirai, a malware popular for infecting IoT devices to carry large-scale DDoS attacks.
However, in the case of Github, the DDoS attacks were possible due to a critical security flaw in Memcached servers which was identified Akamai, Arbor Networks, and Cloudflare. According to researchers, implementation of the Memcached servers’ UDP protocol is flawed and anyone can launch a major DD0S attack without much ado.
The researchers call it an amplification attack. Github, on the other hand, has confirmed that it was an amplification attack using the Memcached-based approach that peaked at 1.35Tbps via 126.9 million packets per second.
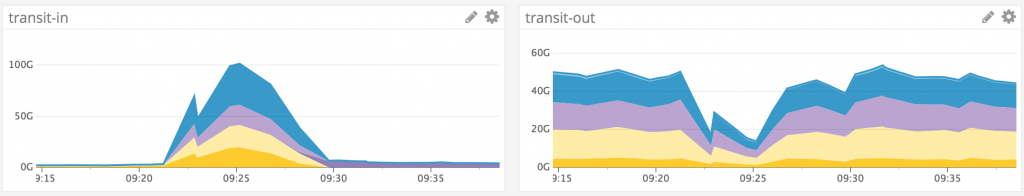
If hackers manage to prepare the amplification attack well, they can launch an attack with lowest possible IP spoofing capacity, as low as 1Gbps, and successfully launch very large attacks that can reach up to hundreds of gigabits per second.
In its blog post, Github’s Sam Kottler explained the attack and wrote that “Spoofing of IP addresses allows Memcached’s responses to be targeted against another address, like ones used to serve GitHub.com, and send more data toward the target than needs to be sent by the unspoofed source. The vulnerability via misconfiguration described in the post is somewhat unique amongst that class of attacks because the amplification factor is up to 51,000, meaning that for each byte sent by the attacker, up to 51KB is sent toward the target.”
According to Cloudflare’s engineer Marek Majkowski, “Over the last couple of days, we’ve seen a big increase in an obscure amplification attack vector — using the Memcached protocol, coming from UDP port 11211. Unfortunately, there are many Memcached deployments worldwide which have been deployed using the default insecure configuration.”
“15 bytes of the request can trigger a 134KB of response sent to the unfortunate target. This is amplification factor of 10,000x! In practice, we’ve seen a 15-byte request result in a 750kB response (that’s a 51,200x amplification).”
To mitigate the attacks Github decided to use Akamai’s Prolexic which provides fully managed DDoS protection and as expected Akamai filtered and blocked the malicious traffic packets. Moreover, Github has apologized to its users and maintained that at no point was user data at risk. The company vows to improve its security to handle such large-scale cyber attacks.
If you are running a business; do not forget to calculate the cost and probability of a DDoS attack on your business with this DDoS Downtime Cost Calculator.
