The latest global malspam campaign targets the hotel industry, emphasizing the need to stay alert against such attacks at all times.
Cybersecurity researchers at Sophos X-Ops have issued a warning to the hospitality industry about a sophisticated malspam campaign targeting hotels worldwide. The campaign leverages social engineering tactics to lure hotel representatives into opening password-protected archives containing malware designed to steal sensitive data.
A malspam attack is a cybersecurity threat where malicious actors send emails containing malware to infect your device and steal your data or disrupt your system. Imagine a spam email filled with not just junk, but hidden traps waiting to ensnare you. That’s essentially what a malspam attack is.
According to researchers, attackers are targeting hotels worldwide with email complaints about service problems (e.g. allege violent attacks, bigoted behaviour, and theft of items) or requests for information (e.g. asking for accommodation for someone with allergies, business support, or accessibility for disabled or elderly guests) to create an aura of legitimacy before sending links to malicious payloads.
The malspam campaign was reported just days after FortiGuard Labs researchers identified a similar campaign targeting unsuspecting users with a fake hotel reservation/booking scam. In this campaign, scammers compromised devices using the MrAnon Stealer.
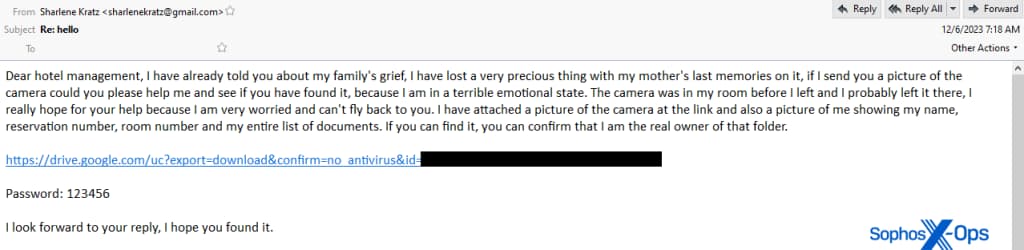
These emails contain links to password-protected archives hosted on public cloud storage platforms like Google Drive. The password, often simple (e.g., “123456”), grants access to the malware, primarily of the Redline Stealer or Vidar Stealer families. It utilizes obfuscation techniques like password protection and jump commands to evade detection. Additionally, large file sizes (larger than executables) often containing zeroes as spacefill are used to prevent analysis.
Sophos researchers identified that the attackers are using the same methodology that they discovered in April 2023. The emails typically span a wide range of subjects that can be broadly categorized into complaints about serious issues faced during a recent stay at the hotel and requests for information for future bookings.
Either way, the attackers send links to malware payloads wrapped in password-protected archive files, posing a threat to hotel representatives. In every case, the threat actor provided documentation as proof of their complaints, which contained malware. These messages are engineered to play on emotions. For instance, in one of the messages, the sender asks for help locating a camera with photos of a deceased relative.
In another sample, the threat actor claims to have already booked rooms through the website but needs accommodation for a family member with a disability with a link to a ZIP file containing medical records. The threat actor adds that the link may only be compatible with Windows computers.
Most samples have a code-validation certificate, with some being new or fake. Endpoint protection tools may exclude valid certificates from scanning, or only check for the presence of a certificate. The malware connects to a Telegram encrypted messaging service URL.
The bot then downloads a payload from the URL and uses HTTP POST requests to submit telemetry about the infected machine. The malware does not establish persistence on the host machine, only runs once, extracts and exfiltrates data, and quits. The bot profiles the machine and sends information about it to the bot controller.
Sophos X-Ops has retrieved over 50 unique samples from cloud storage hosted by threat actors conducting the campaign. Most samples displayed few detections in Virustotal. Sophos has published IoCs (indicators of compromise) to their GitHub repository.
Sophos’ principal threat researcher Andrew Brandt shared the following comment with Hackread.com on the malspam campaign, explaining the risks it entails for the hospitality industry.
“An attack like this, that takes advantage of well-meaning hospitality managers, could not only cause problems for the hotel but also the guests staying there. Hotel managers hold (in some cases, literally) the keys to everything that happens on the premises, and their passwords give them access to a lot of non-public information about staff, guests and visitors.
“The malware used in these attacks isn’t particularly sophisticated. Once the criminals behind these attacks have stolen passwords, they can use these credentials to gain access to additional hotel assets or sell the credentials to other criminals. While this attack is aimed squarely at hotel managers, the compromised privacy of hotel guests – general consumers – is collateral damage.”
“Guests rely on the discretion of hotel staff for a variety of reasons, but an attack like this takes away the hotel staff’s ability to protect customers from cybercriminals who could misuse the stolen credentials. Hotel staff and front-line managers should be on alert for the unique and unusual characteristics of this attack. In addition, they should note that the spammers in this campaign do not have, and (when asked) will refuse to provide reservation details in the body of the message but may attempt to convince hotel employees that such information is embedded in the linked, malicious archive file.
“In situations where the person contacting the hotel refuses to provide basic information in the message itself, such as the name of the registered guest, their dates of stay, or reservation number, be wary. The use of password-protected archive files as a delivery method is another giveaway that something is seriously amiss.
“Hotel IT managers should deploy multi-factor authentication everywhere it is practical and push policies to Windows computers that change the default setting in Windows that conceal the file suffix for known file types. That way security teams can deliver training and messaging about file extensions (.exe or .scr, among others) that are dangerous for staff to open. And finally, all computers used to communicate with guests should have adequate endpoint protection software.”
RELATED ARTICLES
- Booking.com Scam Targeting Guests with Vidar Infostealer
- Silent Ransom Group Utilizes Callback Phishing for Network Hacks
- USPS Delivery Phishing Scam Exploits SaaS Providers to Steal Data
- Iran’s MuddyWater Group Hits Israelis with Fake Memo Spear-Phishing
- LinkedIn Phishing Scam Exploits Smart Links to Steal Microsoft Accounts