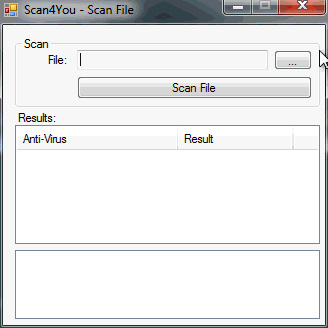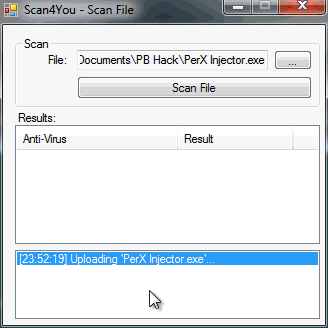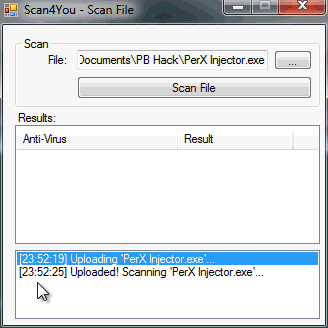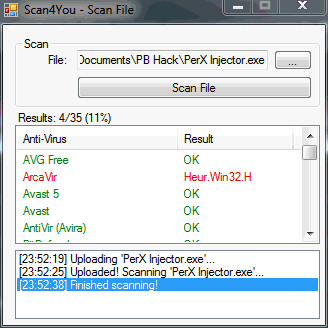
Scan4You was a VirusTotal like platform used for malicious purposes.
A 37-year old male from Riga, Latvia has received 14 years sentence for creating and running Scan4You, a counter antivirus service that aided malware developers to check detection rates of their malicious software.
The convict has been identified as a Latvian non-citizen namely Ruslan Bondars because he was the citizen of the ex-USSR. The Alexandria federal court declared him guilty on 16 May after a co-conspirator claimed that in the past he had worked with the Russian law enforcement authorities.
Bondars is convicted for running Scan4You, a multi-engine virus scanning tool just like Google’s legitimate web service VirusTotal. Using this service, hackers were able to run their code through various mainstream antiviruses before launching them officially into an actual malware campaign.
See: Hackers behind Mirai botnet to avoid jail for working with the FBI
“Ruslans Bondars helped malware developers attack American businesses,” said Assistant Attorney General Benczkowski. “The Department of Justice and its law enforcement partners make no distinction between service providers like Scan4You and the hackers they assist: we will hold them accountable for all of the significant harm they cause and work tirelessly to bring them to justice, wherever they may be located.”
“Ruslans Bondars designed and operated a service that provided essential aid to some of the world’s most destructive hackers,” said U.S. Attorney Terwilliger. “This prosecution demonstrates our commitment to combating global computer crime by taking away the essential tools upon which hackers rely.”
The purpose was to assess whether the malicious code was detected or not during routine security checks. Scan4You is also regarded in the infosec industry as a non-distribute-scanner. The difference between VirusTotal and Scan4You is that the latter doesn’t let antivirus engines to report back results to vendors and the malware detections are kept discreet while the former does so.
Services like Scan4You allow hackers to fine-tune their malicious software so that the malware is able to evade detection when launched in a campaign. Trend Micro reported earlier in 2018 that the convict developed this service in 2009 and it quickly became one of the most sought-after services among the hackers fraternity.
However, Trend Micro has claimed that Bondars has remained an active member of the hacker community since 2006. He started off as an Eva Pharmacy member, which was one of the oldest and largest pharmaceutical spam groups of that time. Bondars was also involved in the distribution of spam messages for providing illegal prescription drugs and distributing the ZeuS and SpyEye banking Trojans.
The Scan4You service, according to the court documents, was hosted on Amazon Web Services servers while malware developers used to pay to get full access to its features. Trend Micro also stated that Bondars also made a very common mistake that almost every malware developer has made in the past, which is that he blocked antivirus engines from the reporting of file scans.
See: 15 years prison for man who hired attackers to DDoS his ex-employer
By 2012, he and some other operators even started ignoring the blocking of URL scans conducted from the Trend Micro engine. For about five years, Trend Micro received queries related to URL reputation from Scan4You and similar services. This data helped the company identify malware campaigns even before these were launched.
After sufficient evidence was obtained, Trend Micro notified law enforcement agencies including the FBI about its findings after which Bondars was arrested in May 2017 with one of his co-conspirators Jurijs Martisevs. Both the cybercriminals were arrested from Riga, and extradited to the United States to face the charges. It was Martisevs whose PayPal account was used for the processing of payments from malware authors. Using this information the accused were easily traced and arrested.
It was later revealed that Bondars was responsible for managing technical infrastructure and Martisevs handled customer support through email, Skype, ICQ, and Jabber. Bondars was charged after a quick 5-day trial in May 2018 and was declared guilty by the court.