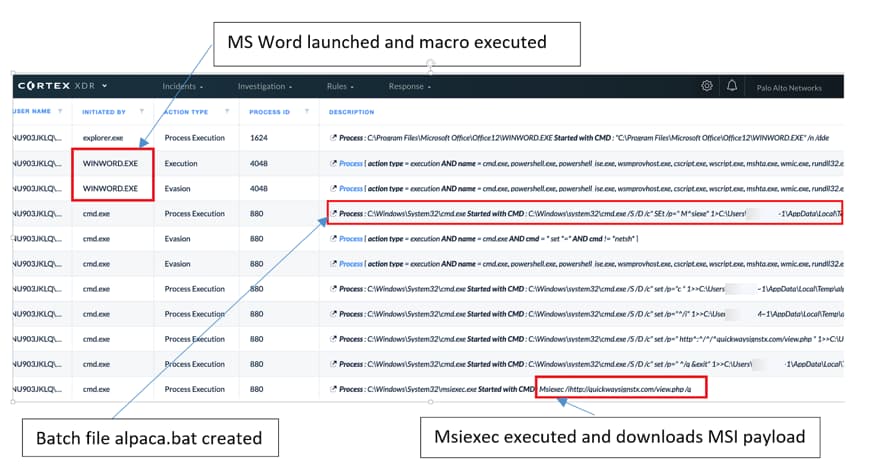
Before dropping NetSupport Manager RAT, attackers lure users into opening a malicious MS Word document by entering a password.
Phishing has always been one of the most popular ways for attackers to gain access to a system. This is despite its relative simplicity as compared to other attacks. In line with this, recently researchers from Palo Alto Networks’s Cortex XDR have come across a new phishing campaign whose aim is to infect users with NetSupport Manager RAT (remote administration tool).
Although NetSupport is not malicious in itself and is used for legitimate purposes normally such as network administration, attackers here are misusing it for their own motives of gaining remote access. The campaign is believed to have been running from November 2019 to January 2020 and specifically targeted at the print and film industry.
Attack Process
How they do so is by sending emails with a malicious Word document that claims to contain important information and a password alongside for opening it.

According to a blog post published by researchers, these were mostly sent “using a random protonmailcom email address and contained email subjects related to refund status or unauthorized credit card transactions” according to the researchers.
See: Hackers clone ProtonVPN website to drop password stealer malware
Moreover, the users are told that they need to enable macros within Microsoft Word to enter the password.
Since the user is in most cases curious about knowing what’s in the document, they do so which results in malicious code being executed, and hence the building up of command strings.
These strings are obfuscated through the use of labels on VBA which are then used to launch a file named cmd.exe and construct a batch file by the name of alpaca.bat which in return is executed to install a “Microsoft Intermediate Language (MSIL) binary to the victim.”
Moving on, it checks if either AVG or Avast is running on the victim’s machine. If they are, the entire process is stopped there otherwise it continues. We do wonder though why other antivirus software is not checked for instead of these 2 specifically.
Proceeding, the malware then installs the “NetSupport Manager RAT” and send the location of the victim’s computer to “‘geo.netsupportsoftwarecom” completing its attack since now a connection has been established.
Conclusion
This is not the first time that we’ve seen NetSupport Manager being used for unintended purposes. Researchers from Palo Alto Networks and Zscaler have also reported similar cases in April 2018 and November 2019 respectively.
See: Luminosity RAT author pleads guilty to creating & selling hacking tool
Our recommendations remain the same that everyone avoids opening attachments from unknown emails, using good anti-virus software and also avoid being curious especially when tempted by random USBs left out in the public or anonymous emails like in this case above.
Did you enjoy reading this article? Kindly do like our page on Facebook and follow us on Twitter.