Microsoft has warned of a sophisticated phishing scam, accompanied by the use of a custom backdoor called MediaPI, orchestrated by the Iranian Mint Sandstorm APT.
Microsoft Threat Intelligence has reported that Iran-linked threat actors, including Mint Sandstorm (APT35 and Charming Kitten), are targeting high-profile researchers working on the Israel-Hamas conflict through phishing scam led by a sophisticated social engineering campaign.
The campaign aims to gather diverse perspectives on the conflict by targeting those working at universities and research organizations. Mint Sandstorm, a subset of Iran‘s intelligence arm, the Islamic Revolutionary Guard Corps (IRGC), specializes in compromising sensitive information from high-value targets through resource-intensive social engineering campaigns.
According to Microsoft’s research, a subset of Mint Sandstorm, PHOSPHORUS, has been targeting high-profile individuals working on Middle Eastern affairs at researchers associated with academic research organizations and universities in the UK, USA, Belgium, France, Gaza, and Israel since November 2023.
Microsoft has observed new tactics in this Mint Sandstorm campaign, including using compromised email accounts to send phishing lures, connecting to its C2 server using the Client for URL (curl) command and delivering a custom backdoor called MediaPl.
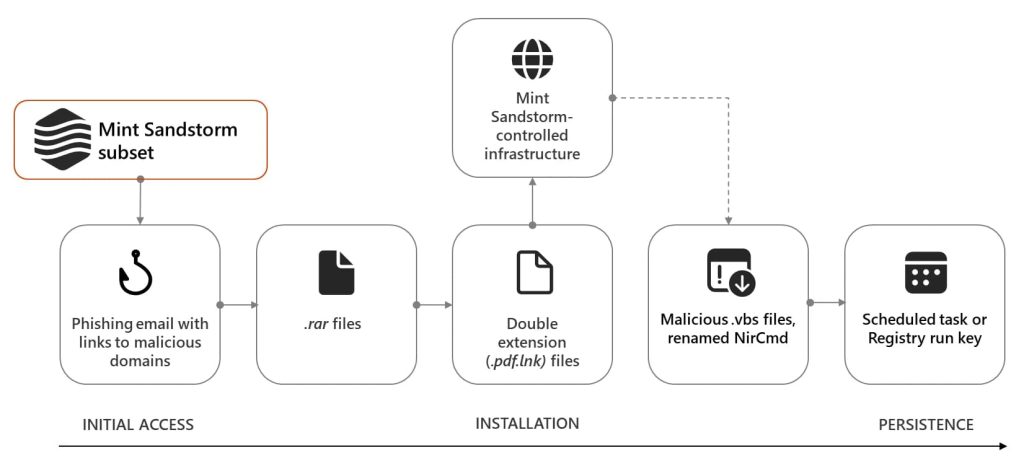
The threat actor uses spoofed email addresses to impersonate journalists and send benign emails asking for their review or feedback on an article on the Israel-Hamas war. They used legitimate but compromised email accounts belonging to the individuals they seek to impersonate.
If someone falls for the lure, Mint Sandstorm sends another email containing links to malicious domains that lead them to sites like cloud-document-editonrendercom to retrieve a RAR archive file supposedly containing the draft document.
The.rar file is decompressed into a double extension file (.pdf.lnk) and launches a curl command to retrieve malicious files from attacker-controlled subdomains of glitchme and supabaseco.
Microsoft observed multiple files downloaded to targets’ devices in this campaign, including several.vbs scripts and a renamed version of NirCmd. The attacker uses a malicious file, Persistence.vbs, to persist in compromised environments.
The campaign may have further bolstered Mint Sandstorm’s credibility and contributed to its success. The tradecraft involves impersonating known individuals, using bespoke phishing lures, and benign messages in the initial stages.
Research indicates that Mint Sandstorm is continually improving and modifying its tools to target desired environments, potentially allowing it to maintain persistence and evade detection.
Microsoft recommends implementing mitigations to reduce the impact of Mint Sandstorm campaigns. This involves training end-users against clicking URLs in unsolicited messages, and disclosing/sharing their credentials, as well as checking for poor spelling and grammar in phishing emails and spoofed app names.
Microsoft also encourages users to use web browsers that support SmartScreen to identify/block malicious websites and scams. Also, enable network protection to block connections to malicious domains and IP addresses. Cloud-delivered protection can cover rapidly evolving attacker tools and techniques.
For insights, we reached out to Balazs Greksza, a Threat Response Lead at Ontinue. “Actors like APT35 have primary goals around geopolitics, national security, and counter-intelligence and in tense situations military preparedness and in the general understanding of economic and trade practices; however sanctioned countries have a more difficult time to influence.,” said Balazs.
“Actors like APT35 have primary goals around geopolitics, national security, and counter-intelligence. In tense situations military preparedness and in a general understanding of economic and trade practices; however, sanctioned countries have a more difficult time influence,” Balazs explained.
RELATED ARTICLES
- Iran’s MuddyWater Group Targets Israelis with Fake Memo Phishing
- Iran’s Scarred Manticore Targets Middle East with LIONTAIL Malware
- Iran’s Peach Sandstorm Deploy FalseFont Backdoor in Defense Sector
- Iranian Hackers Posed as Israelis in Targeted LinkedIn Phishing Attack
- Microsoft reports two Iranian hacking groups exploiting PaperCut flaw
