Lazarus hackers are believed to be backed by the North Korean government.
The IT security researchers at Sansec have reported that North Korea backed Lazarus hacking group might be involved in stealing credit card information from mainstream European and US-based eCommerce stores since May 2019.
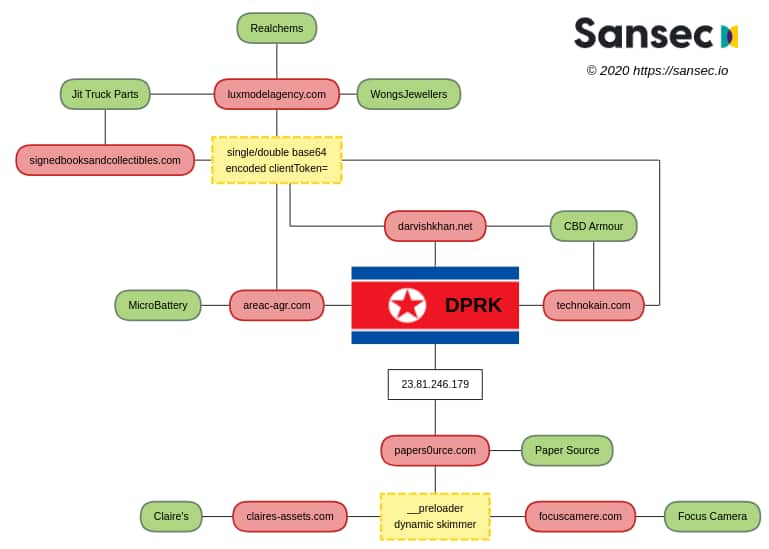
According to the latest report from Sansec, the hackers planted digital skimming code in the payment card information systems used by large retailers to make money for the Kim Jong-un regime. The claim does hold weightage as the UN reported back in 2019 that North Korea made $2bn only through cyberattacks.
See: How Bad is the North Korean Cyber Threat?
Lazarus’s name is largely associated with cyberattacks on cryptocurrency exchanges and banks, and this is the first time it is accused of targeting retail stores. As per the report from the security firm Group-IB, Lazarus managed to steal over $600m worth of crypto between 2017 and 2018.
Sansec reports that Lazarus is involved in attacks on several dozen large-scale retail stores. Their targets include the high-profile accessories retailer Claire’s, Focus Camera, Wongs Jewellers, CBD Armor, Jit Truck Parts, Paper Source, Realchems, and Microbattery.
Stealing payment card information from online stores’ customers is called the MageCart attack. In this attack, cybercriminals use web skimmers, also called malicious scripts, to copy sensitive credit card data from the checkout page.
In this case, however, it is still unclear how Lazarus hackers could access their target stores’ back-end systems. It is speculated that they used spear-phishing against the retail outlet’s employees.
As per Sansec’s report, Lazarus has developed a “global exfiltration network” where they hijack and repurpose legitimate websites to disguise their malicious acts and exfiltrate the stolen data.
Sansec researchers could identify many exfiltration nodes in Lazarus’ network in the past few months. They claim that in their campaign against eCommerce stores, Lazarus hijacked websites of a New Jersey-based bookstore, Lux Model Agency in Milan, and a Tehran-based vintage music store. Another tactic they use is registering the same domain names as their target store.
It is worth noting that credit card skimming and specifically scripts like Magecart can result not only in the loss of one’s payment details but also other crucial information such as phone numbers, home addresses, and security codes.
See: Major Magecart skimming attack hits 8 local US government sites
Therefore, website owners running carts should watch out for MageCart attacks and follow these steps to protect their platforms from such attacks.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.