The Xamalicious Backdoor can gain complete control over a targeted Android device without detection by the device’s security solution.
McAfee’s Mobile Research Team has uncovered a widespread Android backdoor threat, dubbed Xamalicious, showing sophisticated tactics to compromise user devices. The malware has exploited the Xamarin framework, employing its capabilities to hide malicious code within the APK file build process, enabling it to operate undetected.
This threat aims to gain accessibility privileges through social engineering, communicating with a command-and-control server to download a second-stage payload injected at runtime.
Once installed, the malware takes full control of the device, enabling various fraudulent actions such as clicking on ads, installing apps, and other financially motivated activities without user consent.
Financial Motivation Unveiled:
What sets Xamalicious backdoor apart is its direct connection to the notorious ad-fraud app, “Cash Magnet.” This link exposes a financially motivated agenda behind the attacks, as Cash Magnet engages in automated ad clicks, app installations, and other actions to generate fraudulent revenue.
Ubiquitous Distribution and Persistent Threat:
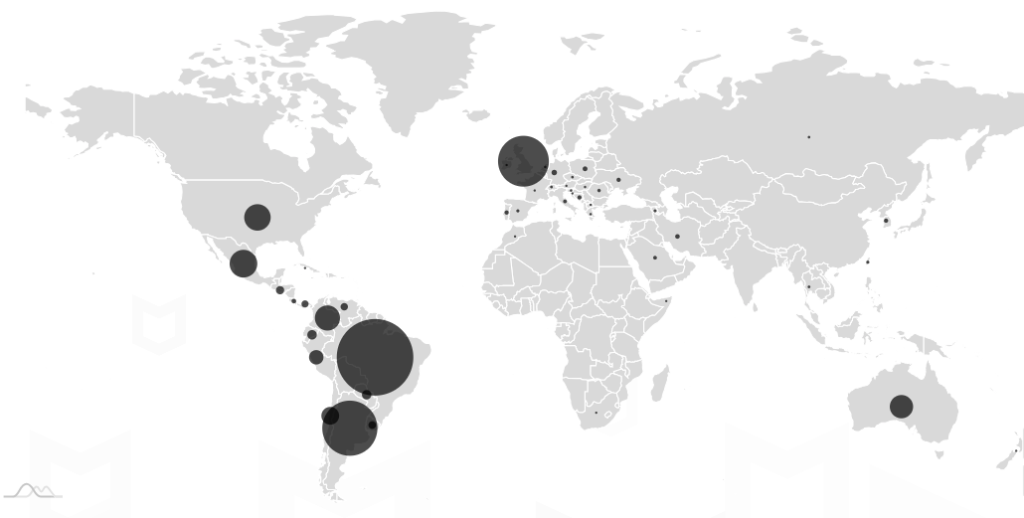
According to the McAfee Mobile Research Team’s blog post, approximately 25 malicious apps carrying Xamalicious backdoor have been identified, some of which infiltrated Google Play since mid-2020. Despite Google’s proactive removal of these apps, the threat persists through third-party markets, compromising over 327,000 devices.
The impact of this threat is far-reaching, affecting users across continents. The most significant activities have been observed in the USA, Brazil, Argentina, the UK, Spain, and Germany.
Some of the affected apps that McAfee is urging users to delete are:
- LetterLink
- Logo Maker Pro
- Track Your Sleep
- Auto Click Repeater
- Universal Calculator
- Sound Volume Booster
- Sound Volume Extender
- Count Easy Calorie Calculator
- Step Keeper: Easy Pedometer
- 3D Skin Editor for PE Minecraft
- Essential Horoscope for Android
- Astrological Navigator: Daily Horoscope & Tarot
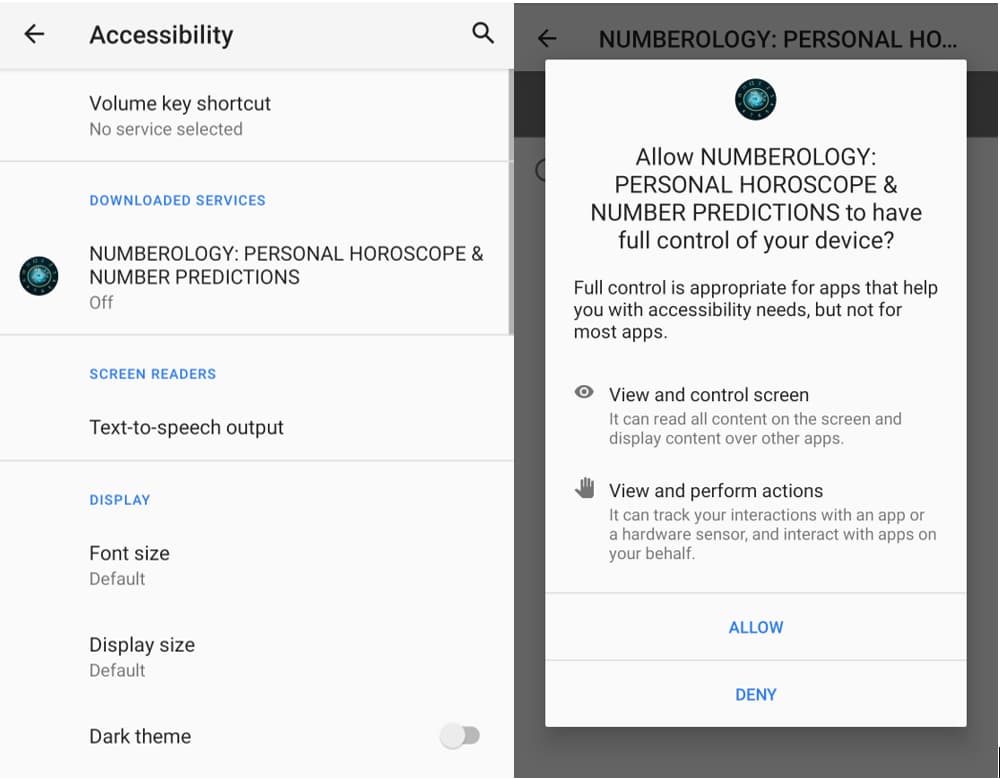
- NUMEROLOGY: PERSONAL HOROSCOPE & NUMBER PREDICTIONS.
Dynamic Second-Stage Payload Raises Alarms:
Once installed, the second-stage payload of the Xamalicious backdoor grants the malware full control over the device. This capability allows the malware to self-update the main APK and execute various activities, from acting as spyware to potentially operating as a banking trojan, all without requiring user interaction.
Exploitation of Accessibility Services:
The modus operandi of the Xamalicious backdoor involves tricking users into granting accessibility service permissions. Exploiting vulnerabilities and prompting users to activate these services despite OS warnings manually, the malware gains a foothold on the device.
Stealthy Data Collection and Encryption:
Xamalicious backdoor goes beyond typical malware by collecting extensive device information and communicating with a command-and-control server. The communication is safeguarded through the use of JSON Web Encryption (JWE) tokens. The malware’s DLL contains hardcoded RSA key values, opening the door for potential decryption during analysis.
Protective Measures for Users:
If you are using Android devices, it is crucial to protect them from the Xamalicious malware and other emerging Android threats. Users are strongly advised to exercise caution when granting accessibility service permissions, particularly when an app does not have a legitimate need.
Installing reputable security software, such as McAfee Mobile Security, is recommended to mitigate the risks associated with malware infections. Regular updates are crucial to ensure ongoing protection against evolving threats in the mobile landscape. Stay informed, stay protected.
RELATED ARTICLES
- Fake YouTube Android Apps Used to Distribute CapraRAT
- Android Malware FjordPhantom Steals Funds Via Virtualization
- Amazon, eBay and Afterpay as Top Android User Data Collectors
- New MMRat Android Trojan Uses Fake App Stores for Bank Fraud
- Android TV Boxes Infected with Backdoors, Hacking Home Networks