WannaCry ransomware attack has left a devastating trail on half of the world and this also includes the Russia’s postal service which was recently targeted and successfully infected by the malware. Some of the service’s computers are still not operational. This is one of the biggest signs of weakness when it comes to Russia’s online defenses and many believe that this might make it one of the major victims of the recent global extortion.
The ransomware attack has compromised the automated management system of the Russian post office and many of the touch-screen terminals ended up being infected. This is mostly because they’re still running on Windows XP, which is considered outdated. It’s still unknown how many branches were affected by the attack.
According to Reuters, Russian Post’s spokesman has stated that no computers were infected during the attack; however, many of the terminals were still turned off, simply as a precaution. Other than that, everything is still stable and in full working order.
Virus #Wannacry hits Russian postal service, exposes wider security shortcomings, Reuters reports. Computers switched off as precaution.
— Xavier Colás (@xaviercolas) May 25, 2017
Among the infected institutions are the Interior Ministry, Russian Railways and even the mobile operator MegaFon. All of these companies have reported being locked out of their computers, with the ransomware note appearing and demanding $300-600 in Bitcoin. Also, there are several reports that the attack hit the Russian central bank and they have confirmed it by stating that some of the Russian banks were indeed compromised but that those are isolated cases.

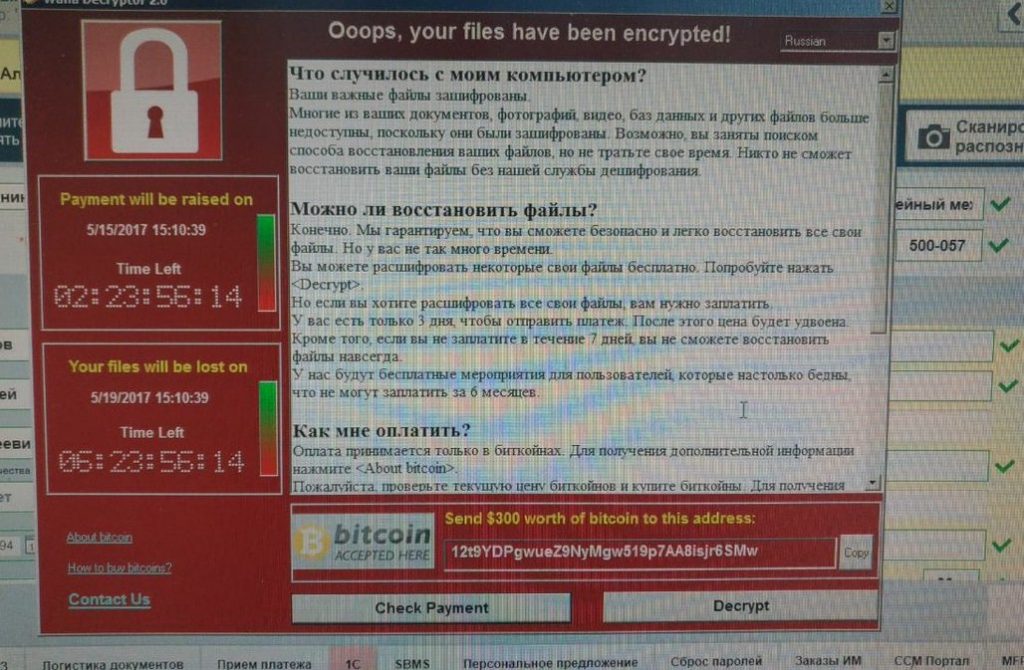
The virus spread easily because users and corporations are still using Windows XP which Microsoft stopped supporting years ago. It, therefore, contains a critical vulnerability in Server Message Block protocol (SMB) of the Windows OS exploited by WannaCry ransomware malware. Experts believe that using the outdated operating system in the critical cyber infrastructure is the perfect ingredient for cybercriminals to conduct their attacks. It must be noted that up to 20% of all of the infected computers were located in Russia.
Investigators have also pointed out that the post office attack shows that WannaCry attackers are not only targeting the ‘important’ computers but pretty much everyone they can find and get access to. This is why all of the systems need to be updated.
Before this attack, Russian postal service has never known any virus related issues as far as it’s publicly known. In this case, workers have revealed that they were instructed not to turn their computers on during the attack and only yesterday received orders to do so. Another post office employee has confirmed that the queuing system was damaged, but they didn’t know the reason why while the second biggest of the Russian mobile operators, MegaFon, has refused to give any comments on how their systems got infected.
Another important fact about this attack is that Russian users come in contact with pirated software quite often which are unlicensed and that’s why their security isn’t updated. Despite this, there were no confirmations of pirated, unlicensed software in any of the Russian government institutions that were infected. However, computer piracy is still a pretty big issue in Russia. Some reports claim that up to 64% of software used in Russia in 2015 was pirated. Of course, not only the companies are to be blamed since most home users are using pirated software as well.
Vishal Gupta, CEO of Seclore commented on the issue and said that:
- “The severity of WannaCry infections in Russia may come as a surprise to some, considering the country is known for its advanced cyber-espionage capabilities. But, sophisticated offensive capabilities aren’t necessarily indicative of a strong defensive posture, partly because a country’s cybersecurity is largely determined by the precautions put in place by non-technical organizations, like post offices. It’s unlikely WannaCry impacted Russian’s Foreign Intelligence Service, but in cases of ransomware, technically sophisticated government agencies aren’t the prime target. Russia is filled with organization’s running highly outdated legacy software, which doesn’t receive regular software updates, making the country a prime target for WannaCry. And, without the proper data-centric security controls in place, targeted organizations stood little chance against the worm once infected.”
At this point, Windows 10 costs around $140.92 in Russia, which is around 8,000 roubles. That’s a fifth of the average monthly wage, which is around 39,000 roubles. It’s not difficult to see why they decided to download it illegally for free simply.
Source: Reuters | Image Credit: Shutterstock/By Julian Santos
DDoS attacks are increasing, calculate the cost and probability of a DDoS attack on your business with this DDoS Downtime Cost Calculator.
