This is the first ever Clipper malware found on Play Store.
Another day another Android malware on Google Play Store – This time the IT security researchers at ESET have discovered a malware known for replacing the content of clipboard on the targeted device. This type of malware is called Clipper malware.
The malware was targeting Android users through a malicious application available on Play Store and its prime focus was to collect login credentials and private keys from the victim’s computer to steal Ethereum funds. The malware can also replace a Bitcoin or Ethereum wallet address copied to the clipboard with the one belonging to the attacker.
See: Tor Proxy Used By Cybercriminals To Initiate Bitcoin Theft
Dubbed Android/Clipper.C by researchers; the malware takes advantage of the fact that cryptocurrency users do not normally enter the addresses of their online wallets manually. Instead of typing, users tend to copy and paste the addresses using the clipboard. That is where the malware replaces the address of the victim with another belonging to the attacker.
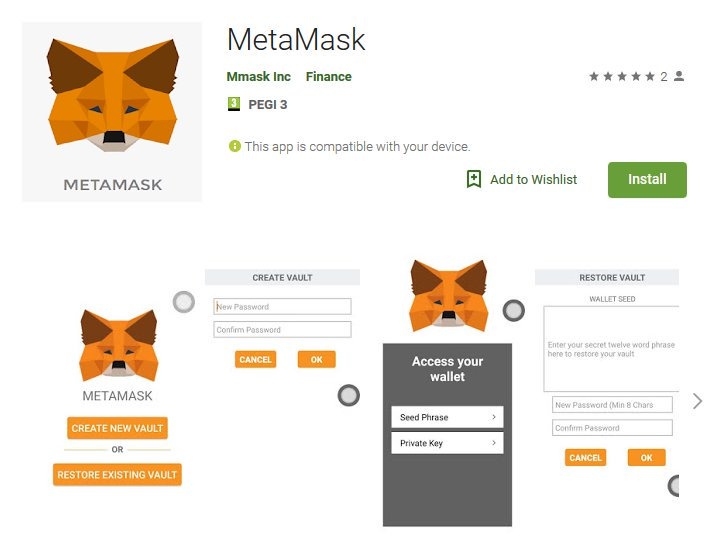
The malware was originally found in the MetaMask app which is a browser plugin that allows users to make Ethereum transactions through regular websites. The plugin is currently available on Chrome, Firefox and Brave browser however the company does not have an app for Android or iOS devices which means that attackers were using a fake version of MetaMask to steal their funds.
It (Clipper) intercepts the content of the clipboard and replaces it surreptitiously with what the attacker wants to subvert. In the case of a cryptocurrency transaction, the affected user might end up with the copied wallet address quietly switched to one belonging to the attacker., said ESET’s malware researcher Lukáš Štefanko.
It is worth mentioning that the clipper malware first appeared in 2017 on Windows platform while in 2018, the malware was spotted in applications on a third-party Android store. Now in February 2019, this malicious clipper is discovered on Google Play Store.
At the time of publishing this article; the malicious app was removed from Play Store after ESET informed Google but the presence of Clipper malware on the Store raises a question mark on the way Google scans applications before allowing them on the marketplace.
A look at BTC and ETH addresses associated with the malware shows that so far attackers have received 0.12868189 BTC which is about $466 while and 0.00909752827411204 ETH which is about only $1.08.
This, however, is not the first time that malware with address replacing capability has targeted users. Previously, “ClipboardWalletHijacker” malware was also found replacing wallet address to steal Bitcoins and Ethereum funds. Moreover, CryptoShuffler Trojan, ComboJack Malware and Evrial Info-Stealing Trojan were also identified replacing wallets to steal cryptocurrency.
See: Popular free Android VPN apps on Play Store contain malware
Android users especially those dealing with cryptocurrency through their Android phones should watch out for this malware as its presence in other apps is quite possible.
Before downloading an app from the Play Store, users are advised to always check the official website of the application developer or service provider for the link to the official app. Otherwise, refrain from downloading the desired app.
Also, avoid downloading apps from third-party stores, keep your device updated and scan it with a trustworthy anti-virus on regular basis. Here is a list of top 10 anti-virus software for 2019 compiled by us. Stay safe online!
Did you enjoy reading this article? Kindly do like our page on Facebook and follow us on Twitter.
