The malware is capable of replacing the victim’s wallet address with one provided by its author(s).
With cryptocurrencies becoming popular in the last couple of years, more and more people have turned to cryptomining hoping to benefit from the boom. In fact, this even led to the price of gaming GPUs rising.
On the other hand, to help people engage in mining, certain platforms exist which make the whole process affordable and convenient. One such example is Hive OS, a software that allows one to manage all their mining computers (rigs) in one place including their installation, updates, security, statistics, and much more.
However, in the latest, an IT security researcher has come across malware that specifically targets the “wallet configuration” file within Hive OS to steal the victim’s cryptocurrencies. It does so by replacing the victim’s wallet address with the “attacker’s.”
SEE: New cryptomining botnet malware hits Android devices
What’s worse is that once this file has been modified, even if the user changes it back to its original state, it would not help since the malware is making updates to the file every 30 minutes.
This was discovered by a researcher from Secure Honey who found a suspicious file while inspecting their SSH honeypot logs.
“The attack starts by changing the Hive OS password to “check” and installing dos2unix (a tool to convert line breaks from DOS format to Unix). The attack then downloads a bash dropper script called “dw” from a remote directory called putkite,” the researcher wrote in a blog post.
The “a.sh” file shown in the screenshot below is of the malicious service itself which also runs a custom miner by the name of “phoenixminer.”
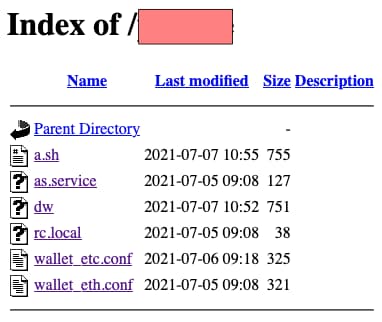
The “a.sh” file shown in the above picture is of the malicious service itself which also runs a custom miner by the name of “phoenixminer.”
Another alarming aspect is that the two scripts used within the attack are completely undetected on VirusTotal allowing them to pass through these systems without any alerts.
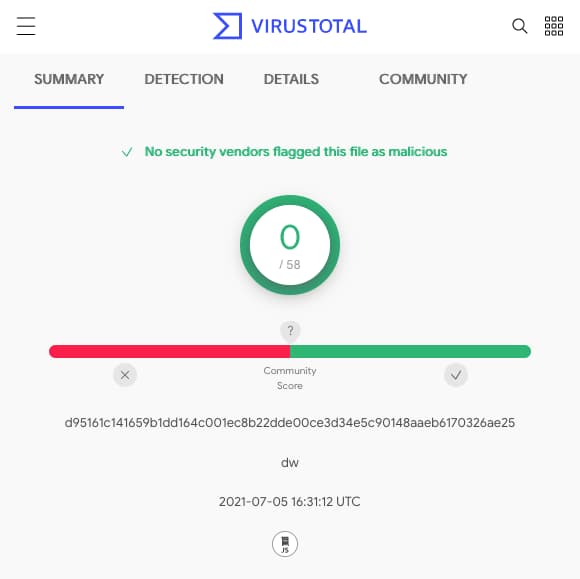
To conclude, for those using Hive OS, it is important to check if any changes have been made to your wallet configuration file without your knowledge.
SEE: ComboJack malware steals cryptocurrency by modifying addresses
If changes are found, the researcher advises to run a command named “service as stop” and remove the malware files which are the following:
- /usr/bin/a.sh
- /lib/systemd/system/as.service
- /etc/rc.local
- dw
- /hive-config/wallet.conf
After this, the configuration file can be safely changed to its original state. In the future, we expect the Hive OS team to issue an advisory notice detailing the security measures they are taking and will take to protect their users.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
