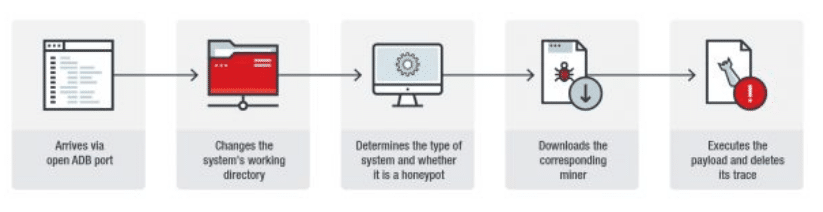
The new malware exploits Android Debug Bridge (ADB) ports.
In a research conducted by the Tokyo-based cybersecurity and threat defense firm Trend Micro, it was revealed that there is a new cryptomining malware bot that’s particularly targeting Android devices. The miner exploits the Android Debug Bridge port system of the device that performs the function of resolving application defects.
It is worth noting that this system is installed-by-default on most of the Android smartphones and tablets. This means, a large number of devices are currently vulnerable to the newly discovered botnet malware. The malware is identified in 21 countries but a majority of the targets were found in South Korea.
The malware attacks a targeted device by exploiting the way ADB ports work in a default setting. These ports don’t need authentication by default and can be distributed to systems that have previously had an SSH connection. SSH connections are capable of connecting almost everything from smartphones to IoT gadgets.
See: Samsung asks users to scan their Smart TVs for malware – Here’s how to
According to Trend Micro, the two systems, once connected, can communicate with each other without needing any authentication once the initial key exchange has occurred. Researchers assessed that this spreading mechanism allows malware to abuse the entire process of creating SSH connections.
The attack then continues to exploit the command shell software for modifying ADB execution permissions and using “wget” command it takes the best pick from three different miners. Afterward, it uses the “chmod 777 a.sh” command for modifying other permissions.
Using the command “rm -rf a.sh*” it manages to stay undetected and even hides its previous and upcoming trails before deleting the download. The attack becomes far more efficient after running new optimizations. The three miners all had the same URL:
http://1989851104:282/x86/bash
http://1989851104:282/arm/bash
http://1989851104:282/aarch64/bash
“To optimize the mining activity, the script also enhances the victim’s memory by enabling HugePages, which will help the system support memory pages that are greater than its default size,” said researchers.
Android is undoubtedly the most used smartphone operating system in the world. Currently, there are billions of Android users worldwide which make the platform a lucrative target for cybercriminals and online scammers. Therefore, be vigilant, keep your phone updated, use trustworthy anti-virus software and scan regularly.
See: 10 Powerful But Not Yet Promoted Antivirus for PC, Mac, Android, iPhone
Furthermore, cryptomining malware are evolving at a rapid pace nowadays and now we have these embedded in Applications available on reliable platforms like Google Play Store. Studies are being carried out to know the extent of the issue and to identify ways for detecting fake apps prior to being downloaded.
Moreover, according to research, thousands of infected applications are uploaded on the online store that deceives users by imitating as the best alternatives to expensive apps.
The researchers used artificial intelligence to detect fake apps and tested them for malware infections and other issues. they examined both the icons designs and description wording and in total, 1.2 million apps were reviewed before they reached the conclusion that Google Play Store has over 2,040 fake copies of popular apps containing malware in a set of 49,608 apps.
See: Cellebrite claims its new tool unlocks almost any iOS or Android device
These apps, as Forbes noted, “showed high similarity to one of the top 10,000 popular apps in the Google Play Store 1,565 potential counterfeits asking for at least five additional dangerous permissions than the original app and 1,407 potential counterfeits having at least five extra third-party advertisement libraries.” The 2000+ most dangerous copies were marked as malware by no less than five commercial use antivirus tools, researchers noted.
Researchers claim that many of these fake copies of popular apps can only be detected by an average user once these have been downloaded and installed unless the user is tech savvy enough to know the difference prior to installation.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.