The source code of Linux.Mirai DDoS botnet has been leaked online — Here are 63 default IoT passwords exposed in the leaked code.
The IoT Botnet Mirai’s source code has been published online by its author along with configuration and set-up details. Naturally, web security analysts are expecting a series of online attacks from malicious threat actors. The reason behind their concerns is that this code can easily convert any hackable, that is, unsecured or unprotected devices like the routers, web cameras and phone, etc., into DDoS Bots. These bots can then be used to attack websites and to take them offline.
Mirai’s code is suspected to be responsible for the attack on Brian Krebs’s KrebsOnSecurity website since Krebs informed public about the publishing of the Mirai code. Krebs warned people about the high probability of the Internet of Things devices getting exploited and hacked in days to come. The code can be used to bombard the websites handling the IoT devices remotely with so many requests that the sites would eventually shut down, rendering the IoT devices vulnerable to exploitation. DDoS attacks play a phenomenally important role in this process.
DDoS (distributed denial of service) attacks have become so common nowadays in the west that the US and UK have become the first and second most targeted countries respectively. DDoS attacks entail flooding the website or a machine with so many requests for information that the device or site becomes unable to function. This makes internet-connected devices enslaved to attackers because these then act according to the commands sent through the botnet or a C&C server. This is how hackers strengthen their ability to conduct successful attacks. In fact, recently we have seen huge attacks, some over 665 gigabits of data per second. This kind of humongous traffic can easily take down any website within a short span of time.
Internet of Things are turning into Botnet of thingsIn this regard, the most important aspect that often gets overlooked is that these IoT devices come with default usernames and passwords, which often becomes an issue while dealing with vulnerabilities. Since these internet connected devices have default credentials that are usually either too easy to guess or too difficult to change so people just choose to let them be. This is a grave mistake as the presence of default credentials would make the job of a botnet much easier.
For instance, the following usernames and passwords can help Mirai botnet, which has been extracted from the published source code:
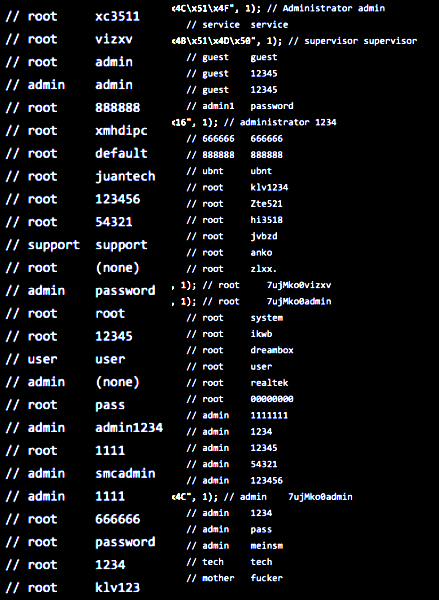
Related: Troubling State of Security Cameras; Thousands of Devices Vulnerable
Firstly, Mirai searches for telnet and then using the credentials we mentioned above to brute force the access to the IoT device such as a DVR, router, camera or the internet-connected hardware. At least two servers are required by the Mirai botnet but the author of the code states that two VPS accounts worked just as fine. Furthermore, it has been observed that around 400,000 devices are connected to Mirai and after the attack on Brian Krebs’ website, the number came down to nearly 300,000.
