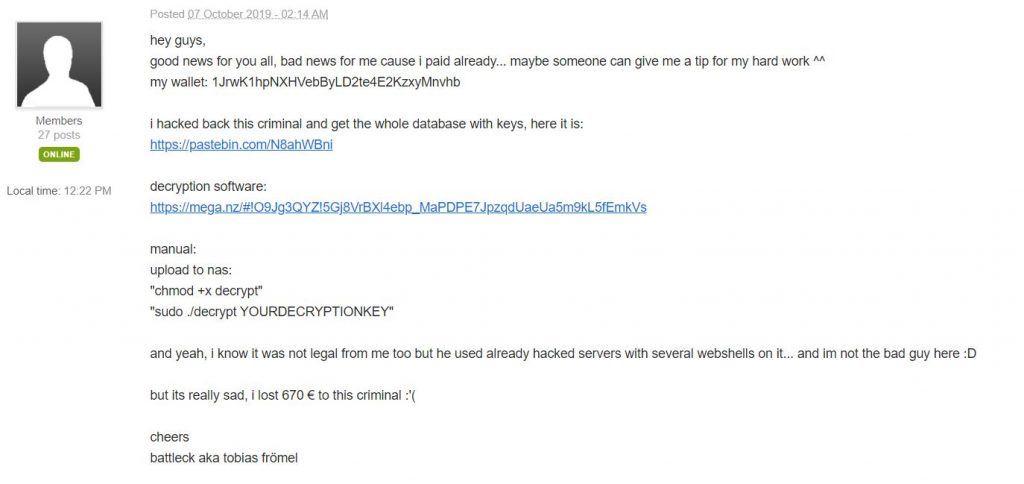
“Hey guys, I hacked back this criminal and got the whole database with (Mushtik ransomware) keys.”
The last laugh – it’s something that everyone would like to have. Turns out, a German programmer by the name of Tobias Fromel had it in a very dramatic fashion.
It all started when he was infected by the infamous Mushtik ransomware which has been used to hack publicly exposed devices network-attached devices (NAS) by QNAP since September encrypting user files with an appended .mushtik extension.
The attacker demanded 0.09 Bitcoins making up approximately 670 Euros or $765. Not the best thing to do. First Tobias paid the amount and then went on to hack the attacker’s command and control server(C&C).
Having gained access, he accessed a PHP script responsible for generating passwords for victims. Using the web shells present, he then created a new PHP file using it to generated Hardware Unique IDs(HWIDs) and their decryption keys alongside which are 2858 to be exact.
Afterward, he shared the entire incident on a support forum for the Mushtik Ransomware attaching links for both accessing the decryption keys and a free decryption software as well.
Users have since confirmed that the decryption keys are indeed legitimate.
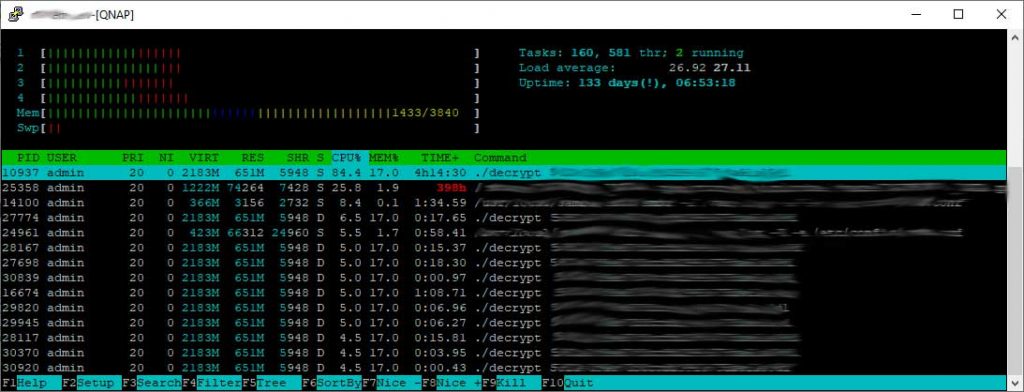
Furthermore, Emsisoft has also released another decryptor software to help users unlock their files easily. An interesting thing though is that by law what Tobias did is illegal. Even though the authorities will not prosecute him most likely for the great service that he has rendered, one may next time look to work with law enforcement agencies when retaliating in this way.
However, a dilemma of further delay does arise from this which may cause many hackers to choose the former faster option. This is further proved by the recent case of Avast collaborating with French authorities which took several months. In this particular case, that would have meant the attacker cashing in on a whole lot of victims meanwhile.
For the time being though, you could head to Twitter to enjoy our hero of the day consoling others with the newly found decryption keys. Also, if you want to understand how ransomware works and how one can prevent its growing threat here is a complete guide compiled especially for Hackread‘s readers.
Did you enjoy reading this article? Kindly do like our page on Facebook and follow us on Twitter.

