The announcement came on Telegram just a week after the RansomedVC ransomware claimed responsibility for hacking the Colonial Pipeline in the United States.
The infamous RansomedVC ransomware group, responsible for a string of high-profile ransomware attacks, has abruptly announced its dissolution. The group, known for its sophisticated hacking tactics and exploitation of the European Union’s GDPR laws, has decided to sell its entire infrastructure.
RansomedVC, which first emerged in August 2023, targeted a wide array of entities, from major corporations to government bodies and educational institutions. Their modus operandi involved infiltrating networks, exfiltrating sensitive data, and subsequently threatening victims with publication of the stolen information unless a substantial ransom was paid. Notably, they also exploited the threat of reporting victims to GDPR authorities, potentially resulting in severe penalties.
The group’s most prominent alleged victims included well-known names such as Sony Corporation and the Colonial Pipeline, victims of the group’s extortion tactics in September and October 2023, respectively.
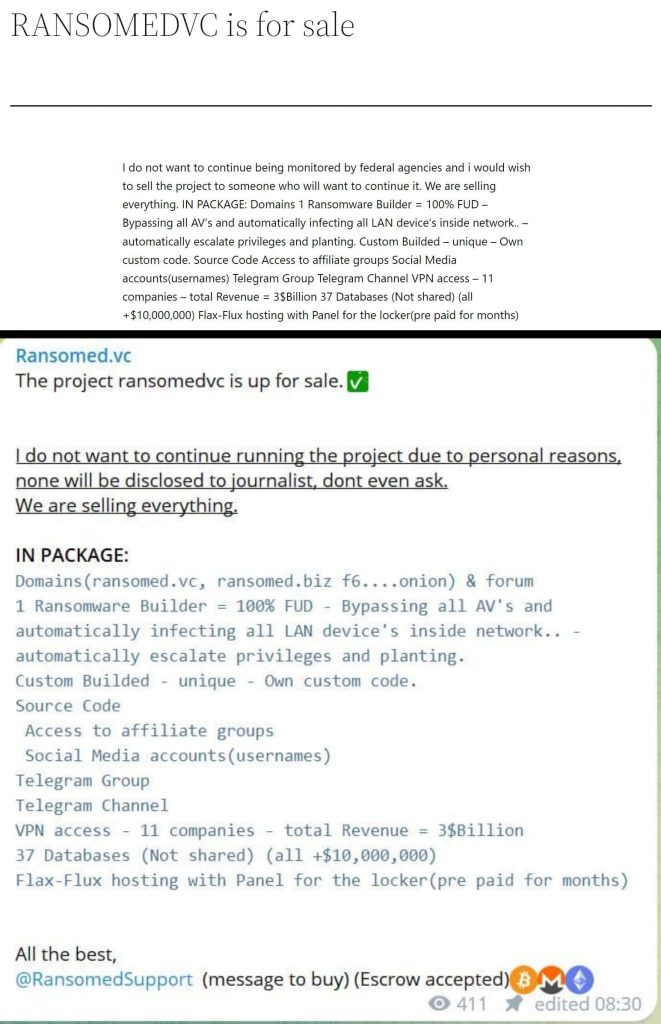
However, RansomedVC has taken an unexpected and unprecedented step by putting their entire toolkit up for sale. As seen by Hackread.com, the sale includes a staggering array of assets, such as various domains and forums, a ransomware builder with promised 100% undetectability by antivirus software, access to affiliate groups, social media accounts, Telegram channels, VPN access to multiple companies with a jaw-dropping revenue of $3 billion, databases worth over $10 million each, and more.
The group’s admin, while announcing the sale on Telegram, mentioned “personal reasons” for the decision but categorically stated that these reasons would not be disclosed to journalists or the public. On their dark web blog, the group’s admin stated they do not wish to be monitored by federal agencies.
“I do not want to continue running the project due to personal reasons, none will be disclosed to journalist, dont even ask. We are selling everything. I do not want to continue being monitored by federal agencies and i would wish to sell the project to someone who will want to continue it.”
RansomedVC
For now, one could only speculate the reasons of the group’s sudden sale. It could be pressure from law enforcement agencies, or even the possibility of a new and more sophisticated cyber operation in the making.
It’s worth noting that on May 6th, 2021, the Colonial Pipeline fell victim to a successful hack by the ransomware group DarkSide. Just days later, on May 9th, the group was compelled to disband after the FBI seized and recovered the Bitcoin ransom paid by the pipeline, leading to their disappearance.”
Nevertheless, depending on who purchases the infrastructure, there is concern about a potential surge in cyber threats and attacks. If you run a business with an online presence, it’s essential to protect it from ransomware attacks by following these simple yet vital steps:
- Regular Data Backup and Recovery: Ensure you frequently back up all your important data and systems to an external device or a cloud-based service. Having a robust backup system in place enables you to restore your data without having to pay the ransom demanded by attackers.
- Use Reliable Security Software: Implement and maintain strong, updated antivirus and anti-malware software on all devices. These tools can help detect and block potential ransomware threats before they can cause harm. Regularly update this software to ensure it’s equipped to handle new threats.
- Employee Training and Awareness: Educate and train employees about the risks of ransomware attacks. Emphasize the importance of not clicking on suspicious links, downloading unknown attachments, or visiting unverified websites. Create protocols for handling emails and files from unknown sources.
- Keep Software Updated: Regularly update all operating systems, software, and applications on your devices. Updates often contain security patches that fix vulnerabilities that cybercriminals could exploit to launch ransomware attacks.
- Network Segmentation and Access Controls: Segment your network and limit access rights. This means restricting user permissions so that each user only has access to the information and resources necessary for their job. This reduces the chances of a ransomware attack spreading throughout the entire network if one device is compromised.