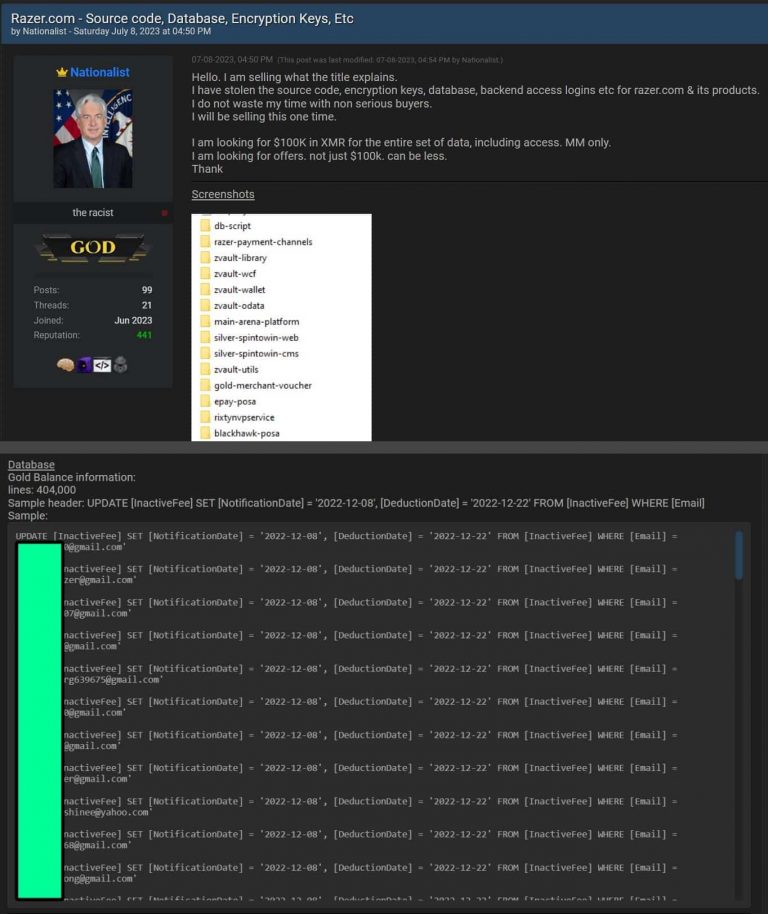
The hacker claims to have stolen Razer’s data, which allegedly includes source code, encryption keys, database access logins, and backend access credentials.
A threat actor going by the online handle of ‘Nationalist’ has claimed to possess stolen data from Razer Inc., a prominent American-Singaporean technology company. The news broke on Saturday when ‘Nationalist’ posted about the purported data breach on newly surfaced Breach Forums.
According to the seller, the stolen information encompasses a wide range of sensitive data, including source code, encryption keys, database access logins, and backend access credentials. To substantiate these claims, the seller provided screenshots displaying a detailed file tree and folders allegedly originating from Razer.com.
In exchange for the stolen data, ‘Nationalist’ requested a payment of US$100,000 in Monero (XMR) cryptocurrency, but also indicated a willingness to negotiate offers below the asking price. Monero, unlike Bitcoin, Ethereum or other cryptocurrencies, prioritizes privacy and anonymity, making it challenging to track the movement of funds and identify those involved.
“I have stolen the source code, encryption keys, database, backend access logins etc for razer.com & its products. I do not waste my time with non-serious buyers. I will be selling this one time. I am looking for $100K in XMR for the entire set of data, including access. MM only. I am looking for offers, not just $100k, can be less,” said the threat actor.
To new readers, this should not come as a surprise, as hacking and cybercrime forums are known for selling high-profile data. Just last month, Hackread.com exclusively reported on how a Russian-speaking threat actor was selling access to a US military satellite to buyers for $15,000.
The authenticity of the alleged cyber attack targeting Razer Inc. has yet to be verified. However, According to the company’s tweet, they are aware of the issue and are currently investigating the “potential breach.
We have been made aware of a potential breach and are currently investigating.
— R Λ Z Ξ R (@Razer) July 10, 2023
It remains uncertain whether the data being sold on Breach Forums is related to the 2020 Razer cyber attack or represents a distinct and recent breach.
As reported by Hackread.com in September 2020, Razer experienced a security incident resulting from a server misconfiguration by its IT vendor, Capgemini. The breach exposed personal and shipping information belonging to approximately 100,000 Razer customers, leading to legal action by the company.
In a comment to Hackread.com, Tom Lysemose Hansen, CTO and co-founder of Promon, a Norwegian cybersecurity company said that “Cybersecurity is no game. You’d have thought that Razer would’ve learnt from its previous blunder in 2020, but this seems to not be the case.”
Tom added that “Gaming-related cybercrime is detrimental to business as the inability to provide a safe and secure experience for customers will erode consumer trust in Razer. Whilst the dust is yet to settle on this one, I think it’s highly unlikely that many people will be signing up for zVault anytime soon.”
As the latest incident unfolds, Razer Inc. faces renewed concerns about the security of its systems and the potential impact on customer data. The company’s response and efforts to mitigate the situation will be closely watched, considering the legal action taken against Capgemini in the aftermath of the 2020 breach.
Users and customers of Razer are advised to remain vigilant and take necessary precautions to protect their personal information. Cybersecurity experts and authorities will undoubtedly investigate the situation to determine the validity of the data breach claims and ascertain the potential implications for Razer Inc. and its stakeholders.
RELATED ARTICLES
- Hackers remotely interrupting GTA Online PC Gameplay
- Fake Super Mario 3 Installers Drop Crypto Miner, Data Stealer
- Minecraft Players on High Alert as Malware Infects Popular Mods
- Fortnite accounts are being hacked to make fraudulent purchases
- Employees at Gaming Giant Activision Hit by SMS Phishing Attack
- Fake ROBLOX & Nintendo game cracks drop ChromeLoader malware