WeLeakInfo.com was home to over 10,000 data breaches containing over 12 billion indexed records.
Hacking in its entirety is a very complex process. Among this, the foremost stage in it revolves around reconnaissance – collecting information about your target. This could be from a variety of sources, both paid and free as well.
One such paid service named WeLeakInfo.com was offering such intelligence to the black hat community for the past 3 years along with at the same time helping users know if their personal data had been compromised.
See: 2.7 billion email addresses & plain-text passwords exposed online
However, it was different from other websites such as HaveIBeenPwned as the latter only lets users know if they had been compromised while WeLeakInfo.com let anyone access that compromised data. How it did this was by storing the data obtained from other websites leaked due to data breaches.
With the number of breaches numbering 10,000 amounting to over 12 billion records as claimed by the site itself, these included plaintext passwords, email addresses, phone numbers, IP addresses, and any other information of that particular person which may have been exposed from a prior breach.
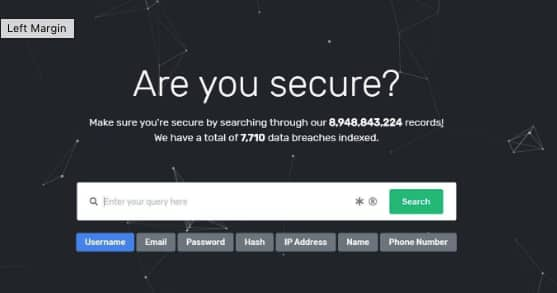
So if you were a hacker, this is how the entire process would work:
1: You identify someone you want to hack by their name, email or username.
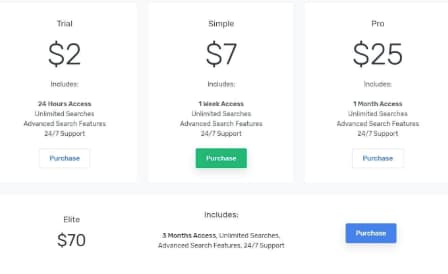
2: You buy a subscription to WeLeakInfo from a range of plans for as low as $2/1.80 Euros.
3: Enter the target’s identifier as noted in step 1 and start discovering their data that may be helpful in hacking them.
See: Dark web’s largest child porn marketplace seized; 338 suspects arrested
This could be something as simple as a plaintext password found that still works or any other information such as a user’s phone number which can be used in social engineering.
“The website had claimed to provide its users a search engine to review and obtain the personal information illegally obtained in over 10,000 data breaches containing over 12 billion indexed records,” a statement from the Department of Justice explained.
While this truly was a goldmine, it fortunately or unfortunately (depending on who you ask) didn’t last for long. On January 15, the FBI in a joint operation with law enforcement agencies from Northern Ireland, the Netherlands, Germany, and the UK seized their domain bringing an end to it.
See: DeepDotWeb, Wall St and Valhalla markets seized by authorities
Moreover, the US Department of Justice in its press release urged people to identify the site’s owners, a task not impossible considering the FBI’s history of apprehending far more anonymity centric criminals such as Ross William, the alleged administrator of the Silk Road marketplace on the Dark Web.
Additionally, although no reports at the moment suggest the involvement of the US, a 22-year-old man in Arnhem has already been arrested with the police stating that certain equipment was found in his home connecting him to the crime at hand.
Yet despite this, Twitterati thought it was a joke calling it a prank being conducted by the site owners.
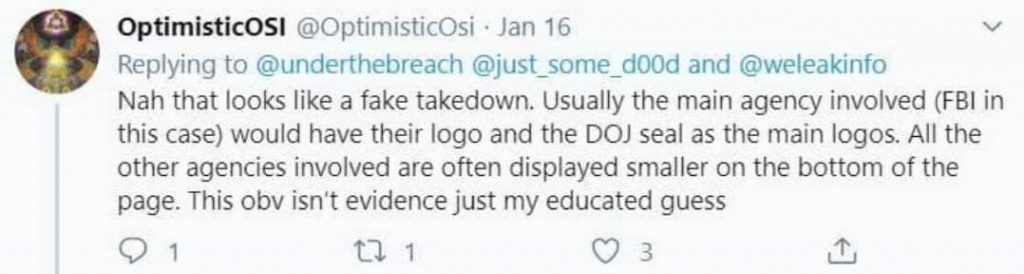
Regardless, you can rest assured that this was indeed a serious operation. We’re now yet to see who was exactly running the wheels behind it, an investigative task that could take considerable time.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.