Israeli members of the armed forces have remained under the radar of cyber spies and espionage actors for a very long time. However, In July last year, over a hundred officials were targeted by malicious cyber-criminals as they managed to compromise their cell phones/tablets and infiltrated data and transferred it to the command and control center. Moreover, the infected devices also received Trojan updates and this helped the attackers conduct further damage to their systems. Now, it is being observed that this campaign is still active and most recent attacks were reported in February 2017.
According to researchers at Kaspersky Labs, this campaign is still in its early stages and mainly affects devices running Android operating system. When a device gets compromised, these turn into spying devices and attackers enact a very sophisticated process of gathering intelligence information by controlling the audio and video capabilities along with collecting GPS data and SMS functions.
More: Pics of IDF women soldiers helped hackers to breach Israeli Military Servers
This particular campaign relies a lot on social engineering and leverages social networks to attract targets into providing classified data and get malicious apps downloaded on their phones. It is worth nothing that only IDF officials are being targeted in this campaign. The attackers are not as technically proficient but have managed to use a variety of social engineering skills. Among the victims are the IDF servicemen from various ranks; a majority of whom are posted on the Gaza strip.
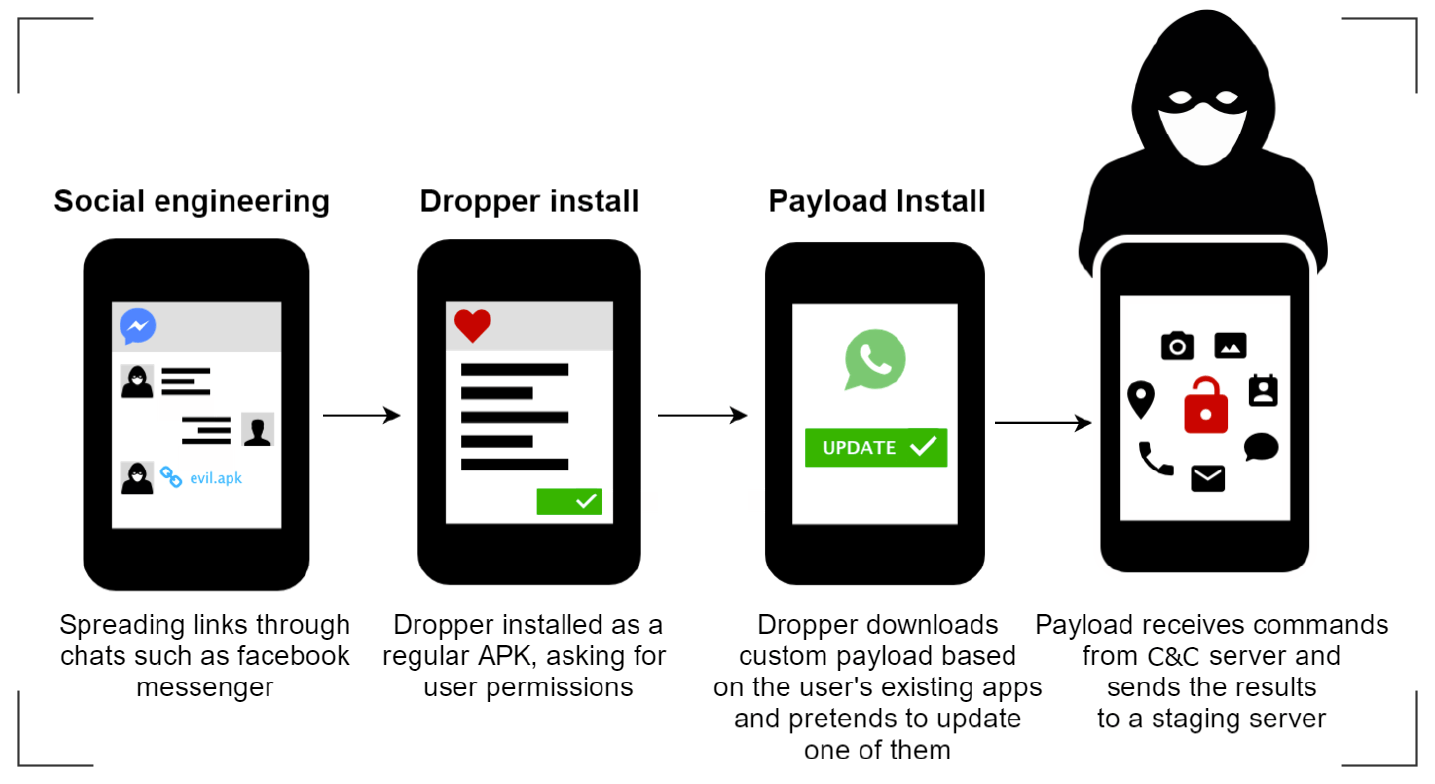
The process of luring victims involves targeting them via social networks and installing malicious apps on their devices by sending them malicious links containing APK file. The victims install the app, which then demands permission to perform some important tasks such as to delete and install packages, write external storage and receiving access to the internet and network state.
The dropper then checks out the configuration server to find out the device model and then selects the kind of payload to be downloaded. It also sends a list of all the applications installed on the phone and a variant will then act as a YouTube layer while some would act as messaging or chat application. One of these payloads is a WhatsApp_Update which can execute manual commands that are triggered by the operator and gathers data from different sources on a regular basis.
The WebSocket protocol is used by the payload to attract a real-time interface and send commands to the payload which resemble a reverse shell. The payload performs checks on the mobile phone after every 30 seconds and keeps collecting data so that every incoming bit of data whether images or SMS and location changes is quickly transferred to the attackers.
More: Hamas Hacked Dozens of IDF Soldiers’ Phones Using Seductive Female Images
Kaspersky Labs stated in its blog post that the campaign is a clear threat for the Israeli DefenseForce/IDF and was specifically launched to get data regarding the way ground forces operate and gather intel on the kind of tactics and equipment used by the IDF.
