Recently, Microsoft was successful in gaining control of 50 domains which were allegedly being used by a North Korean Black Hat group of hackers known as Thallium and APT37 to conduct large-scale cyberattacks.
This news was publicly known when on December 27, a U.S district court released details on the firm’s work and how it authorized them to take down these domains.
See: Indian police & Microsoft busts tech support scam centers
A work of Microsoft’s Digital Crimes Unit (DCU) and the Microsoft Threat Intelligence Center (MSTIC), these targets were primarily based in the U.S, Japan & South Korea and came from a variety of backgrounds. According to Microsoft’s blog post, these targets included,
“Government employees, think tanks, university staff members, members of organizations focused on world peace and human rights, and individuals that work on nuclear proliferation issues.”
The attack was sophisticated and employed effective information gathering using open-source intelligence and then lured users through spear-phishing.
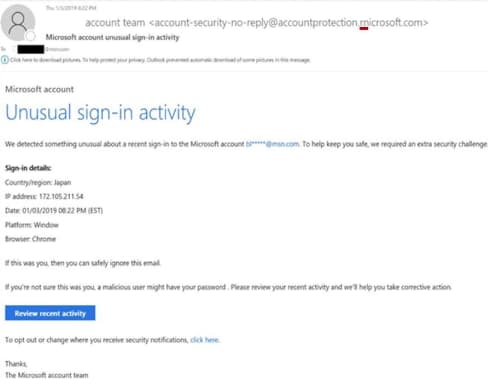
Pictured below is one such example shared by Microsoft where a very legitimate-looking email has been crafted to trick users. Once a user clicks on the button’s link, login credentials are asked for which helps Thallium compromise the user’s account and view all associated activities.
Another interesting trick employed is that they add a mail forwarding rule to the victim’s account automatically receiving every email that the user gets in their inbox without having to maintain access to his/her account. Additionally, the group has also been found installing malware named “BabyShark” and “KimJongRAT” on user systems to extract information.
Yet, it is important to note that this is not the first time the tech giant has taken such action. Prior to this, they have targeted 3 other groups, “Barium, operating from China, Strontium, operating from Russia, and Phosphorus, operating from Iran”.
See: Interview with the Chinese Hacker who hacked Microsoft India Store
These have undoubtedly played a great role in securing the internet and more importantly will continue to serve as a vital part of Microsoft’s CSR role. In light of this, for users, it is recommended that they take basic security precautions such as employing two-factor authentication, having reliable anti-virus software on their devices and keep check of their account’s activity logs.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.

If you’re dumb enough to type in all your info because you receive an email saying you ‘need’ to then you’re dumber than a box of rocks.